
grcacademy.io /feed/
GRC Academy - Governance, Risk, and Compliance Training!
RSS Feed

grcacademy.io /feed/
GRC Academy - Governance, Risk, and Compliance Training!
RSS Feed
You’re CMMC certified… You’ve now entered the final phase of “fire and forget.”
Step carefully… You CAN invalidate your certification by making changes!
Check out these excerpts from the CMMC Program proposed rule:
It is possible for an organization to need a new assessment during the validity period. CMMC self-assessments and certifications are valid for a defined CMMC Assessment Scope.
What is the CMMC assessment scope? The CMMC glossary says it “includes all assets in the contractor’s environment that will be assessed.”
More goodness from the CMMC program rule:
If the CMMC Assessment Scope changes due to infrastructure modifications or expansion of the CMMC Assessment Scope due to new acquisition, a new assessment may be required.
It continues:
The original CMMC certification remains valid for the original CMMC Assessment Scope. The information system(s) in the new CMMC Assessment Scope may not be used to process, store, or transmit CUI for any contract until it is validated via a new CMMC assessment.
There isn’t a CMMC traffic cop checking on this stuff after you are certified, right? Well, yes, that is kind of true…
BUT… Contractors are required to annually affirm that they are still compliant and that their CMMC assessment scope has not changed (ie False Claims Act).
Additionally, the DFARS 7021 proposed rule that was published yesterday will require contractors to:
Notify the Contracting Officer within 72 hours when there are any lapses in information security or changes in the status of CMMC certificate or CMMC self-assessment levels during performance of the contract;
I think this is an attempt for another check and balance. What the contracting officers will do with this information I do not know… But it could mean bad news for the contractor, especially if it is determined that a change invalidated their CMMC certification!
I did submit a comment to the government asking that they define the types of changes that are acceptable and won’t invalidate a CMMC certification. Here are a few scenarios I gave them:
What say you? Do you think contracting officers will be able to handle these reports? Who will they pass them on to?!? So many questions…
Need help on your CMMC journey? We offer CMMC training for defense contractors!
I’m also a VP of Cyber at a small defense contractor. I packaged what I learned over the years into comprehensive CMMC courses focused on the DIB!
If you are just starting your CMMC journey, don’t know what to do next, or just want to make sure you are headed down the right track, check them out!
The CMMC Title 48 DFARS 7021 proposed rule (DFARS Case 2019-D041) was published on 8/15/2024!
The proposed rule includes items, but the most notable is the modification of 𝗗𝗙𝗔𝗥𝗦 𝟮𝟱𝟮.𝟮𝟬𝟰-𝟳𝟬𝟮𝟭 which is the contractual clause that will require CMMC compliance/certification!
This proposed rule also adds a new DFARS provision titled 𝗗𝗙𝗔𝗥𝗦 𝟮𝟱𝟮.𝟮𝟬𝟰-𝟳𝗬𝗬𝗬, “Notice of Cybersecurity Maturity Model Certification Level Requirements.”
This provision (the “7YYY” is a placeholder) will be added into DoD solicitations and will let prospective contractors know what CMMC level will be required to win the contract.
This provision is very similar to DFARS 252.204-7019, “Notice of NISTSP 800-171 DoD Assessment Requirements,” which among other things requires the submission of a NIST 800-171 SPRS score to be eligible for contract award.
So what does this mean you ask?
The CMMC Title 32 program proposed rule was released in December of 2023. DoD just sent the final version to OIRA for review. Once the CMMC program rule is finalized, CMMC assessments can begin. The final rule should be published later this year.
Once this DFARS 7021 rule is finalized, DoD will begin to include CMMC requirements in contracts starting the 3-year phase in period.
The following video describes CMMC’s phase in strategy:
Need help on your CMMC journey? We offer CMMC training for defense contractors!
I’m also a VP of Cyber at a small defense contractor. I packaged what I learned over the years into comprehensive CMMC courses focused on the DIB!
If you are just starting your CMMC journey, don’t kno
“I can’t” is a cybersecurity superpower! Why you say?
Social engineer and pen tester Chris Silvers, CISSP shared the power of “I can’t” with me in this clip:
To expand on this, imagine this:
A social engineer calls the helpdesk. She wants to convince them to reset a user’s password so she can compromise the account.
She tells the helpdesk 1st tier representative a convincing story about how hard her day was and seems to be on the verge of tears… The helpdesk rep feels bad for her and really wants to help.
BUT the organization’s policy forbids the helpdesk from changing passwords because of requests over the phone. Additionally, the 1st tier of helpdesk reps can’t change passwords, so this request would need to be escalated.
Even though the helpdesk rep feels guilty for not being able to help, he tells her “I’m so sorry, but I can’t help you because I don’t have the permissions to change passwords,” and asks her to submit her request through the proper channels.
Social engineers try to manipulate us by preying on our emotions. When a person is influenced by emotions, sometimes logic can go out the window.
There is power in “I can’t.” Or said another way, “least privilege.”
We all know the concept of least privilege, but looking at it from the outcome-based perspective of “I can’t” in a social engineering context really reveals its effectiveness.
When organizations perform risk assessments, they should also evaluate the likelihood and impact of social engineering attacks on high-risk job functions, and apply mitigations through least privilege, separation of duties, and training.
Here are a few security controls that address least privilege:
The clip above with Chris is from GRC Academy podcast episode 24, “How To Stop Social Engineering in Its Tracks with Chris Silvers.” I’d highly recommend checking out the full episode!
We are thrilled to announce that we have partnered with IntelliGRC!
IntelliGRC customers will now be armed with the knowledge from our DIB-focused CMMC Overview Training! The course is THE best solution to fast-track your knowledge of CMMC and will save weeks of research!
It has never been easier to start getting after CMMC! IntelliGRC simplifies the path to compliance, and in 2023, the IntelliGRC platform was used to reach one of the first-ever 110 High Assurance SPRS scores through the Joint Surveillance Voluntary Assessment program!
“This partnership is another step forward in achieving our goal of helping Defense Contractors prepare for CMMC. We are honored to partner with IntelliGRC!” said Jacob Hill, CEO of GRC Academy.
We are thrilled to announce that we have partnered with Carahsoft!
Carahsoft is now offering GRC Academy’s CMMC training courses!
Carahsoft Technology Corp. is The Trusted Public Sector IT Solutions Provider™, supporting Federal, State and Local Government agencies and Education and Healthcare markets.
As the Master Government Aggregator® for their vendor partners, they deliver solutions for Cybersecurity, MultiCloud, DevSecOps, Big Data, Artificial Intelligence, Open Source, Customer Experience and more. Working with resellers, systems integrators and consultants, Carahsoft’s sales and marketing teams provide industry leading IT products, services and training through hundreds of contracts.
“This partnership will greatly expand the reach of GRC Academy, and we couldn’t be more excited to partner with Carahsoft!!” said Jacob Hill, CEO of GRC Academy.
We are thrilled to announce that we have partnered with MSPCyberX!
The MSP Cybersecurity Exchange (MSPCyberX) is a community of MSPs working together with cybersecurity compliance experts.
“In an effort to bring our members great content and be an educational resource for MSPs, MSPCyberX has partnered with GRC Academy. Members at our Participating and Active membership levels will receive a complementary license for GRC Academy’s CMMC Overview Training. All of our members will receive a 30% discount for up to 10 additional members of their organization,” said Brian Hubbard, Founder of MSPCyberX.
“We at GRC Academy are thrilled to provide foundational CMMC training to MSPCyberX members. We are honored to partner with MSPCyberX!” said Jacob Hill, CEO of GRC Academy.
We are pleased to announce that we have recently signed a partnership agreement with PECB! This partnership will deliver significant benefits to enterprises, by providing best practices of ISO standards in North America.
“GRC Academy’s partnership with PECB will greatly expand our course catalog with quality online self-paced training offerings. We are honored to partner with PECB!” said Jacob Hill, CEO of GRC Academy.
“By partnering with GRC Academy we will have the opportunity to provide our customers with the expertise they need to prepare for the future,” said Tim Rama, CEO of PECB. “Our goal in partnering with GRC Academy is to demonstrate how the skills acquired in PECB training courses can be applied to solving daily life challenges, and thereby, how they relate directly to their career interests and aspirations,” added Rama.
GRC Academy will start by offering PECB training for the following ISO/IEC standards:
These courses include exams and respected certifications. GRC Academy also plans to offer discounts to veterans and others who want to transition into cybersecurity!
PECB is a certification body which provides education and certification under ISO/IEC 17024 for individuals on a wide range of disciplines. As a global provider of training, examination, and certification services, PECB offers its expertise on multiple fields, including, but not limited to, Information Security, Privacy and Data Protection, Business Continuity, Quality and Service Management, Risk Management, Health and Safety, and Sustainability.
PECB help’s professionals show commitment and competence by providing them with valuable education, evaluation, and certification against internationally recognized standards. PECB’s mission is to provide their clients with services that inspire trust, demonstrate competence, and benefit society as a whole. For further information about PECB’s principal objectives and activities, visit www.pecb.com.
The United States Department of Defense’s (DoD) Cybersecurity Maturity Model Certification (CMMC) 1.0 didn’t allow Plan of Actions and Milestones (POA&Ms).
According to NIST Special Publication 800-53 r5, a POA&M is “a document that identifies tasks that need to be accomplished. It details resources required to accomplish the elements of the plan, milestones for meeting the tasks, and the scheduled completion dates for the milestones.”
A common response from industry was to ask the DoD to reflect on their own systems, and to allow industry the same amount of flexibility as they do on their own.
The long awaited CMMC proposed rule was released the Friday before Christmas! The rule clearly specifies when POA&Ms are allowed and when they are not.
The CMMC rule differentiates between an assessment POA&M and an operational POA&M.
For purposes of conducting a CMMC assessment and satisfying the contractual eligibility requirements for CMMC Level 1, 2, or 3, an OSA is only permitted to have a POA&M for select requirements scored as NOT MET during the CMMC assessment and only under the following conditions…
CMMC Proposed Rule – https://www.federalregister.gov/d/2023-27280/p-1384
Under CMMC 1.0 no assessment POA&Ms were allowed!
An OSA shall maintain a POA&M, as applicable, as part of operations under the security requirement for Risk Assessments and Continuous Monitoring (CA.L2–3.12.2) for CMMC Levels 2 and 3…
CMMC Proposed Rule – https://www.federalregister.gov/d/2023-27280/p-1384
The DoD understands that issues will occur over time after the assessment, but they want the CMMC controls as compliant as possible at the time of assessment.
I think this makes a lot of sense. Although the contractor will be required to submit annual affirmations of continued compliance, CMC doesn’t have an RMF-like continuous monitoring capability where the government has at least periodic insight into the detailed security state of the system (in this case the organization).
If you come out of your CMMC level 2 or level 3 assessment with a POA&M, you must complete all of the findings within 6 months.
“If the POA&M is not closed out within the 180-day timeframe, the Conditional Level 2 Certification status will expire.”
CMMC Proposed Rule – https://www.federalregister.gov/d/2023-27280/p-1314
This also applies to CMMC level 2 self-assessments and CMMC level 3 certifications.
And if you have an active contract with CMMC requirements, “standard contractual remedies” will apply, and the OSC will be ineligible for additional awards” within the impacted CMMC assessment scope.
Our friend Shauna Weatherly of FedSubK.com provided context to what “standard contractual remedies” could include:
Those [standard contractual remedies] would be up to the agency, but I could see variations from a price adjustment in favor of the agency to contract termination for default (T4D), depending on how egregious the issues are, the contractor’s effort (or lack thereof) to correct, and impacts to the Government mission.
Under a Cost-plus-Award-Fee (CPAF) or Cost-plus-Incentive-Fee (CPIF) type contract it could result in a loss of fee, depending on the structure or basis of fee payments.
Under Performance-Based Contracts, maintaining compliance could be an element in the Quality Assurance Surveillance Plan (QASP) and result in reduced contract payments.
It would also most likely result in an overall negative past performance rating in CPARS, or at the very least negative ratings for specific CPARS element(s), which follows a contractor for three years for source selection purposes as they seek new awards.
Shauna Weatherly, founder of FedSubK.com, retired 35-year federal acquisition professional
Timing here is very important. If a C3PAO or DIBCAC was involved in the assessment, they have to perform a POA&M closeout with you. Depending on the controls that were POA&M’d, that might require another onsite visit and more time to accomplish the closeout.
I imagine there will be many companies that run into problems because they delayed closing out their assessment POA&M.
The controls that are allowed to be POA&M’d can be easily viewed on our CMMC control explorer. They are also listed below.
POA&Ms are allowed under certain conditions:
POA&Ms are not allowed for any of the following 1-point controls:
POA&Ms are allowed under certain conditions:
Cannot POA&M any of the following controls:
After years of waiting the CMMC proposed rule has been published on the Federal Register! This proposed rule is a HUGE milestone and is the precursor to seeing CMMC requirements in contracts.
The comment period for the rule and notice ends on 2/26/2024.
Here are the links:
GRC Academy has submitted the following comments:
You can easily download the CMMC guidance documents at the following OneDrive share:
DoD plans to phase in CMMC over 4 phases. We expect to see CMMC begin appearing in contracts earliest late 2024.
If you’d like to know more about the rulemaking process, check out these GRC Academy podcast episodes:
We are working hard to update our CMMC Overview course based on the new rule! We expect the course updates will be complete by the second week of January.
We have also updated our CMMC control explorer based on this rule!
GRC Academy is pleased to announce that our CMMC Overview Course is now available for sale to government personnel on GSA Advantage!
To date our course has received 33 5-star reviews! The course has been described as “outstanding,” “extraordinary,” and “amazing”! We are very thankful for the positive feedback!
Just like contractors in the Defense Industrial Base (DIB), government personnel in the Department of Defense (DoD) need to understand CMMC and the many contractual and cybersecurity requirements behind it.
If you serve as a Contracting Officer, Contracting Officer Representative, Program Manager, Information Systems Security Manager, or any other role that is responsible for developing requirements for DoD contracts or managing defense contractors, this course is for you!
Our founder Jacob Hill worked for the government for nearly 5 years at Marine Corps Systems Command. During that time, he supported an IT procurement shop where he worked closely with contract specialists. Jacob has completed DAU courses and achieved DAWIA level III in IT, and level I in PM, and he also served as a COR and Project Manager.
Most recently Jacob has been serving as the Director of Cyber Operations at a small business in the DIB and has been developing a cybersecurity program in preparation for NIST 800-171 and CMMC.
Jacob has seen both sides of the fence, and he believe GRC Academy’s CMMC Overview course will greatly benefit the Department of Defense as they prepare to implement CMMC into contracts.
For those that follow privacy news, you have probably noticed a trend in the United States – multiple states have proposed and passed their own privacy laws, creating a complex patchwork of compliance requirements. In fact, as of the time of writing this article, over a dozen states have passed their own privacy laws, providing residents of certain states with privacy rights, requiring businesses to have a Privacy Policy with specific disclosures and requiring businesses to follow certain rules when collecting and processing personal information.
With more privacy laws being passed every day and more requirements being imposed, it is no surprise that businesses are having difficulties meeting all of their obligations. In this article, we’ll break down how the privacy law patchwork came into place, what you need to know about these new privacy laws and how US privacy laws compare to other privacy laws such as GDPR.
Seeing that over a dozen states have their own privacy laws, one may wonder, why is that the case? Why doesn’t the United States have a federal privacy law?
The truth is that the United States has multiple federal privacy laws such as HIPAA, the Privacy Act of 1974, FERPA, the CAN SPAM Act, and FINRA. However, these federal privacy laws only protect very specific personal information such as financial information or health information and apply to very specific circumstances such as email spam, education or information collected and retained by the government.
At the time of writing this article, there is no federal privacy law in the United States that protects information such as names, emails, phone numbers, or IP addresses that is regularly collected by businesses online.
While multiple federal privacy bills such as the American Data Privacy and Protection Act (ADPPA) have been proposed in the past, they have not been passed into law. Thus, due to pressure from consumers and consumer rights groups, increased privacy violations and concerns, and new technologies that impact privacy, many states have taken it upon themselves to propose and pass legislation to protect the privacy of residents of their states, creating the state privacy law patchwork we see today.
Many US-based companies started their privacy compliance programs with the requirements of GDPR in mind and may be wondering how they can adapt their program to comply with the new privacy laws in the United States.
It is important to note that GDPR follows an opt-in model, meaning that personal data cannot be processed unless an individual has specifically agreed to the processing of their personal data or if another exception applies. On the other hand, the new privacy laws in the United States follow an opt-out model, where data processing can take place unless a consumer has specifically stated that they do not want it to take place or have opted out of such processing.
In addition, it is also important to note that the new US privacy laws target specific privacy harms such as targeted advertising, the sale of personal information, use and disclosure of sensitive personal information, and profiling whereas GDPR views privacy harms in a more broad sense. Thus, your GDPR compliance program will need to adapt to avoid the specific harms enumerated in these new US privacy laws.
Finally, while following a GDPR compliance program will help you comply with some of the requirements of these new privacy laws, it is important that you also incorporate the specific requirements of the new privacy laws into your GDPR compliance program so that you achieve full compliance.
Due to a lack of a federal privacy law that would adequately protect consumers, the following privacy laws were passed:
If the above seems like a lot to keep track of, you should also be aware of the fact that over a dozen states have proposed their own privacy bills as well, which means that the patchwork will only grow in the future. The most important thing that you can do to prepare for these new privacy laws is to first determine which of these privacy laws apply to your business as that will help you determine the requirements and standards that you need to meet to comply.
Each state privacy law is different, with different thresholds as to who they apply to, different Privacy Policy disclosure requirements, and different compliance obligations. For example, some privacy laws apply if you collect the personal information of residents of certain states, while others apply if you do business in those states, while others require you to meet a certain revenue or data processing threshold. However, these privacy laws also have some similarities:
Lastly, it is important to note that the requirements of each privacy law may change through amendments, rules and regulations so it is important to not just have a compliance program that meets the requirements of the privacy laws as they are currently in place, but to also have a strategy to keep your program up to date with future requirements.
While many have high hopes for the ADPPA, the bill has failed in the past and is now being considered for reintroduction. Currently, that reintroduction is being stalled by the fact that some lawmakers are considering adding provisions related to artificial intelligence into the bill.
For the time being though, businesses should be aware that without a federal privacy law that preempts existing state laws, the state privacy bill patchwork in the United States is not going away any time soon.
If you do not currently have a Privacy Policy or do not have a strategy to keep it up to date with new legislation, make sure to check out the Termageddon Privacy Policy generator, which automatically updates your policies for new legislation.
Want to learn more? Check out episode 7 of the GRC Academy podcast where Donata speaks about privacy laws in detail!
We are pleased to announce that GRC Academy has partnered with Credly!
Credly digital badges will be issued to everyone who completes GRC Academy owned courses!
This is an important step to further enhance the value that our students receive and the credibility of the platform!
Students who have already completed our CMMC Overview course will receive emailed instructions from Credly with instructions to claim your CMMC Overview Course digital badge.
NIST is updating the series of special publications (SPs) dedicated to the protection of controlled unclassified information (CUI) on nonfederal systems. The first update is to NIST SP 800-171. The latest version of NIST 800-171 is revision 2, and this update would result in revision 3.
On July 19th, 2022, NIST issued a 90-day pre-draft call for comments that would be used to inform revisions of NIST SP 800-171, NIST SP 800-171A, NIST SP 800-172, and NIST SP 800-172A.
On November 1st, 2023, NIST released their analysis of the more than 60 individuals and organizations who submitted comments. The chart below is from the document, and shows the sectors and sizes of the commenting entities:

There were a few items in their analysis that are worth highlighting:
The most commented on security requirement was 3.13.11, “Employ FIPS-validated cryptography when used to protect the confidentiality of CUI.” NIST will research and propose options in the forthcoming draft on how best to address feedback on the specific CUI security requirements to balance stakeholder concerns with appropriate countermeasures to protect the confidentiality of CUI.
It is interesting that they would consider offering leniency on the FIPS 140-2/3 requirement for cryptographic modules. NIST operates a program called the Cryptographic Module Validation Program (CVMP) which validates that cryptographic modules operate in accordance with the FIPS 140-2/3 standard. NIST has previously stated that they view crypto modules that are not FIPS-validated as offering no protection at all.
Commenters supported the inclusion of the NFO controls that are currently tailored out. This would result in a more comprehensive set of security requirements in a single source and provide needed foundational context and guidance for the CUI requirements
NIST tailored out 60 security controls and placed them in appendix E of NIST 800-171 r2. NIST refers to this appendix as nonfederal organization (NFO) controls. NIST believes that these controls are so obvious that all complete security program should include them.
Many believe that the appendix is not reviewed by organizations, and therefore many of these NFO the controls are not accounted for. If NIST tailors in the NFO controls, or at least a subset of them, this could drastically increase the number of NIST 800-171’s security controls from the current set of 110 requirements.
NIST wraps up the analysis document by saying that an initial public draft of NIST 800-171 r3 is planned for late Spring 2023. Additionally, they state that the following updates are planned for the forthcoming draft:
- Update the security requirements for consistency and alignment with SP 800-53, Revision 5
(including inclusive language updates), and the SP 800-53B moderate-impact baseline- Develop a CUI overlay (Supplementary Appendix to the existing security requirement catalog) to better link the CUI security requirements to the SP 800-53 controls for stakeholder feedback
- Consider and propose options on how best to address stakeholder feedback on the NFO control tailoring
On February 16, 2023, NIST released a status update on the 3rd revision of NIST SP 800-171. In their statement, NIST stated many changes which are under consideration – here are the most consequential changes:
- Withdrawing requirements that are either outdated, no longer relevant, or redundant with other requirements
- Reassigning some of the NFO controls to the CUI, NCO, or FED tailoring categories
- Adding new requirements based on changes to the NIST moderate control baseline in SP 800-53B and the reassignment of selected NFO controls
- Combining requirements where appropriate for greater efficiency
- Adding organizationally-defined parameters to selected requirements to achieve greater specificity of control requirements
- Adding a CUI Overlay appendix using the controls from SP 800-53, Revision 5 and the tailored moderate baseline from SP 800-53B
The (1) withdrawing of outdated requirements will be beneficial. Some of NIST 800-171’s guidance needs to be brought up to date with NIST’s latest guidance, such as password management.
The (2) reassignment of “some of the” NFO controls to the CUI tailoring category will impact the number of security controls.
The (5) addition of organizationally-defined parameters (ODPs) will bring NIST 800-171 closer to NIST 800-53’s format. ODPs are in the text of the control, such as “Lock the computers screen after [organization defined amount of inactivity] minutes of inactivity.
ODPs allow for more control of the security controls at the organization level by allowing policies and procedures to populate the ODPs. ODPs do provide another layer of complexity when managing the security requirements, but they also offer an opportunity for automation.
The (6) CUI overlay appears to be a simple reference that is similar to the existing appendices in NIST 800-171 r2.
NIST released the draft of NIST 800-171 r3 on May 10, 2023. The draft was very well received by the community. Although there are still 110 controls, there are some notable changes. NIST highlighted the changes in a FAQ, and provided a detailed analysis of the changes.
Here are some additional interesting changes:
- Addition of the “Planning” family.
- Addition of 3.15.2, “System Security Plan.”
- Addition of 3.12.5, “Independent Assessment.”
- Change 3.5.3, “Multi-factor Authentication,” to be required for all accounts no matter the access method.
- Previously it was only required for access to privileged accounts and network access to non-privileged accounts.
NIST held a webinar on June 10, 2023 where they highlighted the latest updates of the draft.
The slide deck is here. Here is the overview slide highlighting the significant changes:
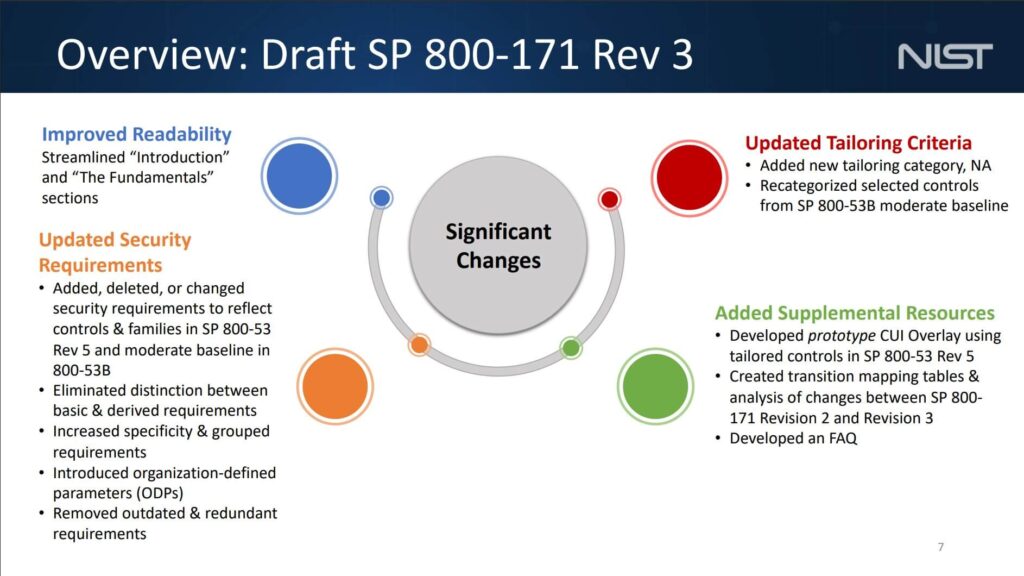
Here is the timeline slide. The slide indicates that NIST 800-171 and NIST 800-171A will be completed in Q2 of FY24.

The DoD’s Cybersecurity Maturity Model Certification (CMMC) is currently in the federal rulemaking process. The output of this process will either be an interim-final rule or a proposed rule.
If the rulemaking process results in an interim-final rule, then we would see CMMC requirements in contracts in 2023. If the rulemaking process results in a proposed rule, then we would likely see CMMC requirements in contracts in 2024.
The release and incorporation of NIST 800-171 r3 is a complication that the DoD doesn’t need during its CMMC rulemaking process. CMMC currently relies on NIST 800-171 r2 and NIST 800-172. The least complex solution for DoD is to push the implementation of the to-be released NIST 800-171 r3 right.
I personally believe it could be a few years before DoD requires the implementation of the to-be released NIST 800-171 r3, however, many CMMC professionals believe that the DoD will begin to require the implementation of NIST 800-171 r3 the moment NIST releases the final version.
DFARS 252.204-7012 is the current contractual driving force requiring the implementation of NIST 800-171. It requires that contractors implement the version of NIST 800-171 in effect at the time of the solicitation, OR as authorized by the contracting officer.
To perform an orderly transition, the DoD could issue guidance requiring the implementation of NIST 800-171 r3 in new CMMC certifications by a certain date, and direct contracting officers to specify NIST 800-171 r2 in contracts until that date. This would allow the bulk of organizations to obtain their initial CMMC certifications under NIST 800-171 r2, and then recertify under NIST 800-171 r3. Historically, the DoD has used this approach when new revisions of NIST SP 800-53 have been released.
To perform an orderly transition, the following documentation (among others) would need to be updated:
Additionally, NIST has indicated that there will be updates to NIST 800-172 (and NIST 800-172A), the document which DoD will pull its CMMC level 3 requirements from. From what we know today, NIST has not yet begun to update NIST 800-172, so the final version of NIST 800-172 and NIST 800-172A could be released in 2024.
These NIST SP updates do complicate the situation for DoD, and it will be very interesting to see how they handle this. Once the new CMMC rule is released, they will be able to communicate how they will address this.
I was trying to log into my isc2.org account, and completely bypassed the MFA I had in place – by accident.
For this vulnerability to be exploited, the following must have been in place:
The attacker could compromise the user’s (ISC)2 account by entering the user’s credentials, registering a phone number during the login flow, and then using the text messaged code.
The video below discusses and demonstrates the issue.
I was logging into the isc2.org site to vote on their recent controversial bylaws amendment proposal when I accidentally discovered the MFA bypass. (ISC)2 is the organization behind the very popular CISSP certification, which is a highly regarded cybersecurity certification.
I had registered an authenticator app to use as MFA, but hadn’t registered text messaging as a method because… Well, text messaging isn’t secure (ie SIM swapping).
The site let me “Try something else” and REGISTER a NEW phone number – I was in! I just bypassed my own enrolled MFA method!
I haven’t been able to confirm this, but it appears this issue was caused by a SSO upgrade that ISC2 made on their website on 7/27/2022.
I reported the issue to them on Tuesday, 10/25/2022, and they called me on Friday, 10/28/2022, to ensure they understood my report. It appeared that they resolved the issue in mid-November, but I finally received confirmation that the issue was resolved on 12/13/2022. I did ask for the exact date that they resolved the issue for my report, but (ISC)2 said they wouldn’t release any further information.
In case you missed it, here is the video demonstration of this issue.
Here is the configuration of my MFA methods prior to the MFA bypass. Note that I only have “Google Authenticator” enabled.

Here I am at the (ISC)2 login screen.

After entering my username and password, the system prompted me for me a code from the authenticator app. I didn’t have access to the code, so I clicked on “Try Another Method.”

I didn’t remember the methods I had set up, so I tried “SMS Authentication” (which actually wasn’t enabled at this time).

Here is the problem. The site allowed me to register a NEW phone number, and enable the SMS MFA method during the login flow. ANY phone number could be used.

Here is the text message I received with the code.

Entering the code I received in the text message.

…And I’m logged in. I just bypassed my own MFA!

The system did generate an alert indicating that a new MFA method had been activated.

Here are the MFA options after enabling “SMS authentication” during the login flow.

1. Strong passwords still matter.
As long as we have deal to passwords, they remain an important defense layer. Even with the recent compromise of LastPass, the recommendation to use a password manager still stands:
2. MFA isn’t a cure-all.
Unfortunately, this isn’t the first time we’ve seen improper MFA configurations on websites. We’ve also seen MFA defeated in different ways such as compromising MFA tokens.
Don’t neglect the importance of strong passwords.
We are proud to announce the CMMC control explorer!
The explorer allows you to easily view, filter, and search through the CMMC requirements. The search crawls through the control summaries and the supplemental guidance as well. It consolidates multiple sources into a single reference, and it includes links to reference documents, the associated points from the DoD assessment methodology, and the assessment procedures from NIST 800-171A.
All of this information is easily accessible – even from your phone.
We hope that you find this tool valuable! Please contact us if you have any suggestions on how to make it better!
This may surprise you, but FedRAMP does not have any US citizenship / US persons requirements.
FedRAMP is a federal program that standardizes federal security requirements for cloud service providers (CSPs). Federal agencies can leverage the CSP’s FedRAMP authorization package which makes it much easier for CSPs to work with the federal government.
You can learn more about FedRAMP by watching the “FedRAMP Overview” video below from our CMMC Overview Training for Small and Medium Businesses (SMBs).
DFARS 252.204-7012 states that cloud systems which the contractor uses to store, process, or transmit DoD CUI must meet security requirements “equivalent” to the FedRAMP-moderate baseline.
This may cause some to believe that a FedRAMP-moderate authorization checks all of the required boxes. It does NOT. If you possess export-controlled information such as International Traffic in Arms Regulations (ITAR), YOU are responsible for ensuring the CSP is staffed by US persons.
We reached out to the FedRAMP office to verify that the there are no US citizenship / US person requirements, and this was the response:

The FedRAMP FAQ page alludes to FedRAMP’s lack of citizenship requirements:
Q: What does FedRAMP require for personnel screening requirements from Cloud Service Providers (CSPs)?
A: FedRAMP requires CSPs to describe their organization’s personnel screening requirements. If an agency has requirements for federal background investigations, or additional screening and/or citizenship and physical location (e.g., U.S. citizens in Continental United States [CONUS] offices only), then those requirements would need to be specified in the solicitation language, which may affect bid pricing.
The FedRAMP office posted a much more direct response on GitHub:
Thank you for your question. As with all FedRAMP authorizations, FedRAMP Tailored does not specify a citizenship requirement as there is no government-wide requirement on citizenship. The only requirement is for the CSP to perform background checks, and the CSP has the freedom to determine exactly what background checks are performed. While a CSP may have non-US persons supporting their system and can still achieve an ATO with some agencies, there are several agencies that maintain their own citizenship requirements. In other words, a CSP using non-US persons is still FedRAMP compliant, but will find their market limited among Federal agencies.
We had an interesting discussion regarding this topic on LinkedIn. A gentleman stated that US citizenship was an early requirement for FedRAMP, but GSA decided to remove it.
We hope that this helps you! If you have any questions, please contact us.
ChatGPT has gone viral since it was released two weeks ago. We decided to ask it to write a story about a plumber who could not get CMMC certified, and… Well, wait for the plot twist!
We also posted this on LinkedIn. Enjoy the story!
Bob was a happy plumber. He loved his job and he was good at it. He had been in the plumbing business for many years, and he had built up a loyal customer base. But everything changed when the Department of Defense started requiring CMMC certification for its contractors.
Bob tried to get certified, but he quickly realized that it was a daunting task. The certification process was long and complicated, and it required a lot of time and money. Bob didn’t have the resources to invest in it, and he was starting to worry that he would never be able to work for the DoD again.
One day, Bob was sitting in his workshop, feeling sorry for himself, when he had an idea. Instead of trying to get CMMC certified, he would run for president. He would use his skills as a plumber to solve the nation’s problems and make the country a better place.
Bob was no stranger to hard work, and he was determined to make his dream a reality. He started campaigning in his local community, and he quickly gained support. People were impressed by his honesty and his common-sense solutions to their problems.
As the campaign progressed, Bob’s popularity grew. He was a fresh face in politics, and he was not afraid to speak his mind. He was a true outsider, and he appealed to people who were fed up with the traditional political system.
Eventually, Bob won the election and became the president of the United States. He used his knowledge of plumbing to fix the country’s infrastructure and make sure everyone had access to clean water. He also implemented new cybersecurity measures to protect the nation from threats.
Bob’s presidency was a success. He proved that anyone, even a plumber, could make a difference if they had the determination and the courage to follow their dreams.
If you are a small business who needs to achieve CMMC certification, don’t quit – check out our CMMC Overview Training!