realciso.io /blog/
RealCISO - vCISO Platform & Cybersecurity Compliance Software
Active Web Watch
Are you a current user of the RealCISO vCISO Platform looking to enhance your cybersecurity strategies, share invaluable insights, and collaborate with like-minded professionals? You’ve found the right place! The RealCISO vCISO Platform Users Group is a dedicated LinkedIn community designed to empower Chief Information Security Officers (CISOs), virtual CISOs (vCISOs), and cybersecurity professionals by fostering a collaborative environment for sharing tips, tricks, best practices, and providing essential product feedback.
Our Mission
In the rapidly evolving landscape of cybersecurity, staying ahead requires continuous learning, adaptation, and collaboration. Our mission is to create a vibrant community where RealCISO vCISO Platform users can connect, share knowledge, and leverage collective expertise to enhance their security posture. Whether you’re looking to optimize your use of the platform, discover innovative security strategies, or influence the future development of RealCISO, this group is your go-to resource.
What You’ll Find Here
- Expert Tips and Tricks: Unlock the full potential of the RealCISO vCISO Platform by accessing a wealth of user-shared tips and shortcuts. Learn how to navigate the platform more efficiently, customize dashboards, automate routine tasks, and integrate with other essential tools to streamline your cybersecurity operations.
- Best Practices: Benefit from the collective wisdom of experienced CISOs and cybersecurity professionals. Share and discover best practices in areas such as risk management, incident response, compliance, threat intelligence, and more. Stay updated with the latest trends and methodologies that can help you safeguard your organization’s assets effectively.
- Product Feedback and Enhancement: Your insights are invaluable in shaping the future of the RealCISO vCISO Platform. Provide constructive feedback, suggest new features, and participate in discussions about product improvements. Engage directly with the RealCISO team and influence the development roadmap to ensure the platform continues to meet your evolving needs.
- Collaborative Problem-Solving: Encounter a challenging security issue? Tap into the collective expertise of the group to find solutions. Whether it’s troubleshooting platform features or addressing complex security dilemmas, our community is here to support you with diverse perspectives and innovative approaches.
- Networking Opportunities: Connect with fellow CISOs, vCISOs, and cybersecurity experts from various industries and organizations. Build meaningful professional relationships, exchange ideas, and explore potential collaborations that can drive your career and your organization’s security initiatives forward.
- Exclusive Content and Resources: Gain access to exclusive content such as webinars, whitepapers, case studies, and how-to guides tailored specifically for RealCISO vCISO Platform users. Stay informed with the latest updates, feature releases, and expert-led sessions that can enhance your cybersecurity expertise.
Who Should Join?
- CISOs and vCISOs: Professionals responsible for overseeing and implementing cybersecurity strategies within their organizations.
- Cybersecurity Managers and Analysts: Individuals involved in day-to-day security operations, threat analysis, and risk management.
- IT Leaders and Decision-Makers: Executives and managers seeking to understand and leverage the RealCISO vCISO Platform to bolster their organization’s security framework.
- Security Enthusiasts: Anyone passionate about cybersecurity who wants to learn more about the RealCISO vCISO Platform and contribute to its community.
Join Us Today!
Become a part of the RealCISO vCISO Platform Users Group and take your cybersecurity efforts to the next level. Share your experiences, gain new insights, and collaborate with a community dedicated to excellence in cybersecurity. Together, we can navigate the complexities of today’s threat landscape and build a more secure digital future.
How to Get Started:
- Request to Join: Click the “Join” button and answer a few simple questions to help us understand your background and how you can contribute to the group.
- Introduce Yourself: Once approved, introduce yourself to the community. Share your role, your experience with the RealCISO vCISO Platform, and what you hope to gain from the group.
- Engage and Contribute: Start participating in discussions, sharing your insights, asking questions, and providing feedback. The more you engage, the more you’ll benefit from the collective knowledge of the community.
We’re excited to have you on board and look forward to building a thriving community together!
Welcome to the RealCISO vCISO Platform Users Group – Your Hub for Cybersecurity Excellence!
The post Welcome to the RealCISO vCISO Platform Users Group! appeared first on RealCISO.
RealCISO offers a web-based, scalable, and cost-effective solution tailored specifically for cybersecurity consultants and vCISOs. The platform’s design aims to make the complex world of governance, risk management, and compliance (GRC) more operable and understandable.
Key Features and Benefits of RealCISO:
- Scalable and Nimble Platform: RealCISO is built to be highly scalable and flexible, accommodating the needs of different organizations and consultants. This adaptability allows users to manage multiple clients effectively from a single, centralized platform without sacrificing efficiency.
- Unified Compliance Approach: The platform recognizes the commonalities across various compliance frameworks, reducing redundancy in compliance processes. This approach allows organizations to leverage work done for one regulation (e.g., SOC-2) to streamline the process for another (e.g., ISO), as highlighted by the significant control overlap RealCISO identifies between frameworks like NIST and ISO.
- Efficiency and Speed: RealCISO eliminates the need for traditional, cumbersome tools like spreadsheets by providing an intuitive interface that simplifies compliance management. Users can quickly see where they stand with different assessments and understand their next steps for achieving full certification.
- Real-Time Insights and Reporting: The platform offers real-time insights and reporting, enabling consultants and organizations to assess compliance status instantly and take actionable steps to close gaps. This feature enhances the ability to manage risks and maintain compliance proactively.
- Cost-Effective and Revenue-Generating: By simplifying the compliance process and making it more manageable, RealCISO allows consultants and vCISOs to serve more clients at reduced costs. This scalability not only saves time but also creates additional revenue opportunities.
- Comprehensive Coverage and Support: RealCISO supports over 2300 companies, reflecting its broad applicability and effectiveness across various industries. The platform’s user-friendly design and built-in support for remediation and risk management make it a valuable tool for both independent consultants and organizational GRC teams.
- Built by Real CISOs for Real Needs: The platform’s development is rooted in practical, real-world experience, making it uniquely equipped to address the genuine challenges faced by cybersecurity professionals today.
RealCISO’s mission is to demystify compliance and make it accessible and manageable for all organizations, regardless of size or industry. The platform’s growth and widespread adoption underscore its effectiveness in helping companies navigate the complex landscape of cybersecurity regulations and risk management.
Article: https://grcoutlook.com/realciso/
The post RealCISO: The Cybersecurity Experts appeared first on RealCISO.
Efficiently assess, build, and manage cybersecurity compliance for your organization or clients with RealCISO.
RealCISO is a cost-effective program management and vCISO platform built for consultants, vCISOs, MSPs, MSSPs, and internal cybersecurity teams. RealCISO’s multi-tenant platform streamlines vCISO services at scale, automating risk and compliance assessments, gap analysis, and customized policy development.
Guided Discovery Process
Start with an intuitive discovery questionnaire tailored for each client.
RealCISO begins with a concise and visually engaging questionnaire to gauge unique cybersecurity needs.
Data-Driven Remediation Planning
Prioritize tasks with a proprietary algorithm for efficiency and effectiveness.
RealCISO develops a list of remediation tasks, assessing their relevance and impact, and prioritizes them to ensure efficient and effective cybersecurity solutions.
Clear, User-Friendly Task Descriptions
Present tasks clearly to facilitate seamless implementation.
Tasks are presented in a straightforward manner, making them easy to understand and actionable across diverse cybersecurity areas.
Comprehensive Task Spectrum
Cover all aspects of a client’s cybersecurity framework.
RealCISO includes tasks ranging from technical controls and administrative procedures to security component configurations.
Deliver Insights to Customers
Meet customer requirements with robust cyber risk assessment capabilities.
RealCISO makes it easy for consultants and professional services firms to assess and manage cyber risk, saving time with guided risk audits that provide risk scores in just a few clicks.
Perfect for Service Providers
Simplify account management with multi-tenant capabilities.
RealCISO allows you to set up and manage individual client accounts effortlessly, with unlimited user accounts and customizable permissions.
Demonstrate Ongoing Value
Track and evaluate your client’s security posture over time.
Monitor progress and demonstrate the tangible value of your services, showcasing improvements in cybersecurity stance over time.
Ultimate Whitelabel Software
Offer a branded, comprehensive cybersecurity service.
RealCISO empowers you to deliver top-tier risk management, compliance frameworks, and remediation plans under your own brand, with a multi-tenant architecture and personalized content frameworks.
vCISO Clients
Provide comprehensive cybersecurity services to your clients.
RealCISO is ideal for vCISOs managing multiple clients, streamlining workflow with multi-tenant capabilities and customizable reporting.
Customizable Reporting
Tailor reports to suit the specific needs of each client.
Provide tailored insights and recommendations, enhancing the value of your services.
Secure Client Data Segregation
Maintain the highest standards of privacy and data protection.
RealCISO ensures client data is securely segregated, crucial for handling sensitive information across various client accounts.
Comprehensive Assessments Based on Compliance Frameworks
Support assessments based on common compliance frameworks.
Whether your clients need to comply with SOC2, HIPAA, or NIST, RealCISO covers it.
Ease of Sharing Reports with Clients
Generate and share detailed assessment reports easily.
Facilitate transparent communication and help clients understand their security standings and necessary steps for improvement.
Enhanced Client Engagement
Engage effectively with clear and actionable insights.
Help clients understand their vulnerabilities and the importance of remediation strategies.
Competitive Pricing
Offer a cost-effective solution for managing multiple clients.
RealCISO’s pricing tiers are designed to scale with your clients’ needs and budget, whether you’re working with small businesses or larger enterprises.
Purpose Built
Enhance your capability as a vCISO with RealCISO.
Designed to make your job easier and your clients’ cybersecurity posture stronger, RealCISO is a comprehensive and secure platform.
Ready to streamline your cybersecurity compliance? Discover how RealCISO can transform your security management today. Contact us for a demo and get started!
The post Cybersecurity Compliance with a Platform, Not Spreadsheets appeared first on RealCISO.
Estimated reading time: 2 minutes
Key Takeaways:
- RealCISO offers a more reliable and bug-free experience compared to Apptega.
- RealCISO is significantly more cost-effective versus Apptega’s.
- RealCISO provides a user-friendly interface, ideal for clients with simple needs.
Choosing the right compliance management software is crucial. Here’s why RealCISO outperforms Apptega in both functionality and cost.
RealCISO vs. Apptega: Functionality Comparison
Apptega: A Buggy Experience
One of the major downsides of Apptega is its backend functionality. Users frequently encounter bugs, such as duplication of notes fields, incorrect sub-controls, and rescoring issues. The cross-walking feature, intended to streamline document organization, often misplaces documents, leading to confusion and inefficiency. For example, security awareness training documents appear under unrelated sub-controls like firewall requirements, causing frustration and extra work for users.
RealCISO: Smooth and Reliable
In contrast, RealCISO offers a more reliable platform. Users report fewer bugs and a more intuitive experience. RealCISO ensures that documents are correctly categorized, saving time and reducing errors. This reliability makes RealCISO a preferable option for organizations seeking a seamless compliance management solution.
Cost-Effectiveness
Apptega: High Price, Low Value
Apptega’s pricing at $13,380 can be prohibitive, especially when considering the numerous issues users face. For clients with simple needs, the platform’s complexity can be overwhelming, making the high cost seem unjustified.
RealCISO: Affordable and Efficient
RealCISO, priced significantly lower, offers a more affordable solution without compromising on quality. This lower cost, combined with a more efficient and user-friendly platform, makes RealCISO a superior choice for businesses looking to manage compliance effectively without breaking the bank.
Conclusion
RealCISO stands out as the better compliance management solution, offering a bug-free, user-friendly experience at a significantly lower cost than Apptega. For organizations seeking efficiency and value, RealCISO is the clear winner.
The post Apptega vs RealCISO: A Better Compliance Management Solution appeared first on RealCISO.
RealCISO for MSPs and MSSPs to Scale vCISO Services
Estimated reading time: 2 minutes
Key Takeaways:
- RealCISO is a premier vCISO platform for MSPs and MSSPs, enabling scalable and efficient cybersecurity services.
- The platform helps ensure compliance with regulations and cybersecurity frameworks.
- RealCISO combines data-driven algorithms with CISO-level expertise, bridging the cybersecurity skill gap.
- Features include customizable reporting, self-guided discovery questionnaires, and easy-to-read dashboards.
- Ideal for service providers seeking a multi-tenant, user-friendly solution with low operational costs and high scalability.
RealCISO is Empowering MSPs and MSSPs to Scale vCISO Services Efficiently
The need for robust cybersecurity management solutions is more critical than ever. RealCISO stands out as a leading vCISO platform, empowering Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) to scale their virtual Chief Information Security Officer (vCISO) delivery with efficiency and effectiveness.
RealCISO’s platform offers a comprehensive solution that ensures clients comply with necessary regulations and cybersecurity frameworks. By providing clear guidance on compliance status and steps to achieve full compliance, RealCISO helps service providers deliver structured cybersecurity services to small and medium-sized enterprises (SMEs) at scale.
Combining Expertise with Innovation
Developed by real CISOs, RealCISO leverages data-driven algorithms combined with that CISO-level knowledge to bridge the cybersecurity skill gap, enabling MSPs and MSSPs to offer new services, increase revenue, and reduce operational costs. This powerful combination allows partners to expand their cybersecurity offerings without incurring significant additional costs.
Enhanced Reporting and Monitoring
The platform’s built-in customizable reporting features highlight security gaps and client progress over time, creating new upsell and business opportunities for MSPs. RealCISO’s self-guided questionnaires help evaluate clients’ cybersecurity postures, aligning their cyber profiles with relevant industry standards, frameworks, and regulations.
User-Friendly and Cost-Effective
RealCISO’s user-friendly interface includes an easy-to-read dashboard and one-click reporting, simplifying the management of cybersecurity services. The platform’s multi-tenant capabilities make it ideal for service providers seeking a solution that facilitates in-house cybersecurity expertise with minimal scalability constraints.
Conclusion
For service providers looking to enhance their vCISO delivery, RealCISO offers a reliable, effective, and scalable solution. By combining security and compliance with innovative features, RealCISO enables MSPs and MSSPs to deliver high-quality cybersecurity services, ensuring optimal performance and compliance for their clients.
RealCISO is transforming the way MSPs and MSSPs manage and scale their cybersecurity services, making it a leading choice for those looking to stay ahead in the ever-changing cybersecurity landscape.
The post Empowering MSPs and MSSPs to Scale vCISO Services Efficiently appeared first on RealCISO.
Developing a HR Security Policy
Estimated reading time: 5 minutes
Human resource security policy is a crucial aspect of any organization’s overall security strategy. It involves the implementation of measures to ensure that employees, contractors, and third-party users understand their responsibilities and are suitable for the roles they are considered for. This policy also addresses the risks that human factors can pose to the security of information.
Without a well-defined human resource security policy, organizations may face significant risks, including data breaches, loss of intellectual property, and reputational damage. This article will delve into the various aspects of human resource security policy, its importance, and how to implement it effectively.
Importance of Human Resource Security Policy
A robust human resource security policy is vital for several reasons. First, it helps protect an organization’s valuable assets, such as intellectual property, customer data, and financial information. By ensuring that employees understand their responsibilities regarding information security, organizations can significantly reduce the risk of data breaches.
Second, a human resource security policy can help foster a culture of security within an organization. When employees are aware of the importance of information security and their role in protecting it, they are more likely to take proactive steps to safeguard the organization’s assets.
Lastly, a well-implemented human resource security policy can help an organization comply with regulatory requirements. Many industries have strict regulations regarding the protection of information, and a human resource security policy can provide a framework for meeting these requirements.
Key Elements of a Human Resource Security Policy
A comprehensive human resource security policy should include several key elements. These elements will vary depending on the organization’s size, industry, and specific security needs. However, some common elements should be included in most human resource security policies.
Roles and Responsibilities
Clearly defining the roles and responsibilities of employees, contractors, and third-party users is a crucial part of any human resource security policy. This includes specifying who is responsible for implementing and maintaining the policy, as well as who is accountable for any breaches of the policy.
It’s also important to define the responsibilities of different roles within the organization. For example, management may be responsible for ensuring that the policy is implemented and followed, while employees may be responsible for reporting any suspected breaches of the policy.
Training and Awareness
Training and awareness are critical components of a human resource security policy. Employees, contractors, and third-party users need to understand the policy, why it’s important, and how to comply with it. This can be achieved through regular training sessions, awareness campaigns, and other educational initiatives.
Training should be tailored to the specific needs of the organization and its employees. For example, an organization that handles sensitive customer data may need to provide more intensive training on data protection than an organization that does not handle such data.
Monitoring and Compliance
Monitoring and compliance are also important elements of a human resource security policy. This involves regularly reviewing and updating the policy to ensure it remains effective and compliant with any changes in regulations or the organization’s operations.
Monitoring can also involve tracking employees’ compliance with the policy and taking corrective action when necessary. This can include disciplinary measures for serious breaches of the policy, as well as additional training or support for employees who are struggling to comply with the policy.
Implementing a Human Resource Security Policy
Implementing a human resource security policy is a multi-step process that requires careful planning and execution. The following steps provide a general framework for implementing such a policy.
Develop the Policy
The first step in implementing a human resource security policy is to develop the policy itself. This involves identifying the organization’s security needs, defining roles and responsibilities, and outlining the procedures for training, monitoring, and compliance.
It’s important to involve key stakeholders in this process, including management, IT staff, and employees. This can help ensure that the policy is realistic, comprehensive, and aligned with the organization’s goals and values.
Communicate the Policy
Once the policy has been developed, it needs to be communicated to all employees, contractors, and third-party users. This can be done through a variety of channels, including email, training sessions, and company-wide meetings.
It’s important to ensure that everyone understands the policy and their responsibilities under it. This may require providing additional training or support for some employees.
Monitor and Enforce the Policy
After the policy has been communicated, it needs to be monitored and enforced. This involves regularly reviewing the policy to ensure it remains effective, tracking employees’ compliance with the policy, and taking corrective action when necessary.
Monitoring and enforcement should be ongoing processes, not one-time events. By regularly reviewing and updating the policy, organizations can ensure that it continues to meet their security needs and comply with any changes in regulations or operations.
Conclusion
A human resource security policy is a vital component of any organization’s overall security strategy. By defining roles and responsibilities, providing training and awareness, and monitoring compliance, organizations can significantly reduce the risk of data breaches and other security incidents.
Implementing a human resource security policy requires careful planning and execution, but the benefits of such a policy are well worth the effort. With a robust human resource security policy in place, organizations can protect their valuable assets, foster a culture of security, and meet regulatory requirements.
Take Control of Your Security Posture with RealCISO
Ready to elevate your organization’s security strategy and ensure your human resource policies are up to par? RealCISO is your go-to platform for managing and understanding your security posture with ease. By simply answering a few questions, you can quickly identify areas for improvement and receive tailored recommendations to mitigate cyber risk. Stay ahead of evolving best practices and compliance requirements with RealCISO’s actionable insights. Don’t let the complexity of cybersecurity slow you down.
Learn More about how RealCISO can help you secure your organization’s most valuable assets today.

The post Understanding Human Resource Security Policy appeared first on RealCISO.
Feature Comparison – Cynomi vs RealCISO
Estimated reading time: 4 minutes
Businesses require robust, versatile, and scalable solutions to protect their digital assets. Two notable contenders in this space are RealCISO and Cynomi, each offering distinct features and benefits. However, upon closer inspection, RealCISO emerges as the more comprehensive and strategically advantageous choice for service providers, like MSPs, MSSPs, & vCISOs, looking to enhance their clients’ cybersecurity posture. Here’s a detailed comparison of the two platforms.
vCISO Platform Client Scaling and User Management
RealCISO shines with its “pay-as-you-grow” licensing model, making it an ideal choice for businesses looking to scale. This model not only supports unlimited clients but also accommodates multi-tier relationships (grandparent-parent-child), which is crucial for organizations with complex customer structures. In contrast, Cynomi, while offering multi-tenant capabilities, lacks the multi-tier functionality and does not clearly define its stance on unlimited user support, marked ambiguously in the comparison.
Assessment Capabilities
Both platforms offer a range of assessments, but RealCISO stands out with its unique offerings and partnerships. It is the only platform that allows users to start an assessment from another with a single click—a significant efficiency booster. RealCISO’s expertise is underscored by its construction in collaboration with leading experts and organizations such as the Department of Defense’s National Center of Cybersecurity for Manufacturing and the British Standards Institution (BSI). These partnerships enhance the credibility and reliability of assessments, particularly in areas like NIST CSF, ISO 27001:2022, and CMMC L1/L2.
Moreover, RealCISO is the sole platform integrated with the CIS Ransomware Readiness Assessment and maintains a partnership with a top 30 CPA firm under AICPA for SOC 2 assessments, further highlighting its robustness in compliance and risk management solutions.
vCISO Platform Marketplace Integration
RealCISO excels with its exclusive marketplace capabilities, enabling organizations to add tailored solutions to their assessments. This functionality not only enhances the adaptability of the platform to specific needs but also fosters a collaborative ecosystem where service providers can showcase their solutions. This is a clear advantage over Cynomi, which does not currently offer marketplace capabilities, vendor additions, or “what-if” solutions on assessments.
Insurance and Compliance
In the domain of cyber insurance, RealCISO again takes the lead by aligning its platform with the requirements of underwriters and insurance carriers. This alignment ensures that businesses can seamlessly integrate RealCISO’s assessments into their insurance application processes, a feature not mirrored by Cynomi.
vCISO Platform Licensing Flexibility
RealCISO’s licensing options are tailored to meet the diverse needs of service providers. From one-time assessments to ongoing management and enterprise licenses, RealCISO offers flexibility with a “pay-as-you-grow” pricing model. This approach allows organizations of all sizes to engage with the platform at a pace that matches their growth and cybersecurity maturity. Cynomi’s approach, by comparison, appears less flexible, particularly in its management and enterprise offerings.
Foundational Strength and Geographic Reach
Founded in 2019 and self-funded, RealCISO has been profitable since its inception, indicating strong financial health and a sustainable business model. Additionally, being based in the U.S. and having a team comprised of former Fortune 500 CISOs and U.S. Department of Defense personnel lends it an edge in understanding and tackling the nuances of global cybersecurity challenges.
Conclusion
Choosing the right vCISO platform is critical for ensuring the security and compliance of any organization. RealCISO, with its comprehensive features, strategic partnerships, and flexible licensing options, stands out as a leader in this space, particularly for businesses seeking a robust, scalable, and integrated approach to cybersecurity. Its forward-thinking features and commitment to user-centric design make it a superior choice over Cynomi, especially for organizations aiming to navigate the complex cyber threats of today’s digital world.

The post A Comprehensive Comparison of vCISO Platforms appeared first on RealCISO.
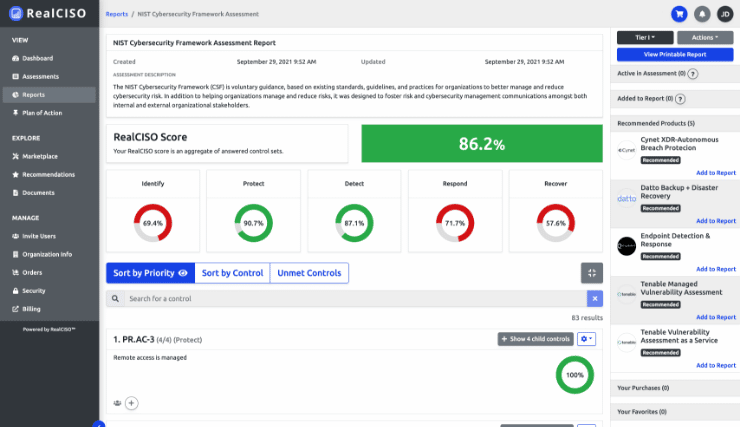
The world of cybersecurity is constantly evolving, with new threats emerging and existing ones becoming more sophisticated. To keep up with these changes, organizations need to adopt robust frameworks that can help them manage their cybersecurity risks effectively. One such framework is the National Institute of Standards and Technology’s Cybersecurity Framework (NIST CSF), which has recently been updated to version 2.0 and is now available in RealCISO.
Understanding the NIST CSF 2.0
The NIST CSF is a voluntary framework primarily intended for critical infrastructure organizations to manage and mitigate cybersecurity risk based on existing standards, guidelines, and practices. However, the framework has proven to be flexible enough to be implemented by non-US and non-critical infrastructure organizations.
The updated NIST CSF 2.0 brings several enhancements over its predecessor, including a more comprehensive approach to privacy and supply chain risk management. It also provides more detailed guidance on self-assessment and continuous improvement, making it a valuable tool for organizations of all sizes and industries.
Key Features of NIST CSF 2.0
The NIST CSF 2.0 is built around six core functions: Govern, Identify, Protect, Detect, Respond, and Recover. These functions provide a high-level, strategic view of an organization’s management of cybersecurity risk.
- Govern – addresses an understanding of organizational context; the establishment of cybersecurity strategy and cybersecurity supply chain risk.
- Identify – assists in developing an organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
- Protect – outlines appropriate safeguards to ensure delivery of critical infrastructure services.
- Detect – defines the appropriate activities to identify the occurrence of a cybersecurity event.
- Respond – includes appropriate activities to take action regarding a detected cybersecurity event.
- Recover – identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event.
Integrating NIST CSF 2.0 with RealCISO
RealCISO is a platform designed to help organizations manage their cybersecurity risks effectively. With the integration of NIST CSF 2.0, RealCISO users can now leverage this robust framework to enhance their cybersecurity posture.
RealCISO provides a user-friendly interface that allows organizations to conduct self-assessments based on the NIST CSF 2.0. The platform also offers a comprehensive dashboard that provides a visual representation of an organization’s cybersecurity risk profile, making it easier for decision-makers to understand and prioritize risks.
Benefits of Using RealCISO with NIST CSF 2.0
Using RealCISO with NIST CSF 2.0 offers several benefits. First, it allows organizations to align their cybersecurity practices with a globally recognized framework. This can enhance their credibility and trustworthiness in the eyes of stakeholders, including customers, partners, and regulators.
Second, it provides a structured approach to managing cybersecurity risks. By following the NIST CSF 2.0, organizations can ensure that they are covering all the essential aspects of cybersecurity, from identifying and protecting assets to detecting, responding to, and recovering from cybersecurity events.
Finally, using RealCISO with NIST CSF 2.0 can help organizations achieve continuous improvement in their cybersecurity practices. The platform’s self-assessment feature allows organizations to track their progress over time and identify areas where they need to improve.
Conclusion
In conclusion, the integration of NIST CSF 2.0 with RealCISO provides a powerful tool for organizations to manage their cybersecurity risks effectively. By leveraging this robust framework, organizations can enhance their cybersecurity posture, gain stakeholder trust, and achieve continuous improvement in their cybersecurity practices.
As cybersecurity threats continue to evolve, it is crucial for organizations to stay ahead of the curve by adopting robust frameworks like the NIST CSF 2.0. With its user-friendly interface and comprehensive features, RealCISO makes it easier for organizations to do just that.
Take the Next Step with RealCISO
Ready to elevate your organization’s security posture with the latest NIST CSF 2.0? RealCISO is here to guide you through the complexities of cybersecurity management. With just a few clicks, you can gain insights, actionable recommendations, and align with top compliance frameworks. Don’t let the evolving landscape of cyber threats slow you down.
Learn More about how RealCISO can simplify your journey to a stronger, more resilient cybersecurity strategy.
The post NIST CSF 2.0 now available in RealCISO appeared first on RealCISO.
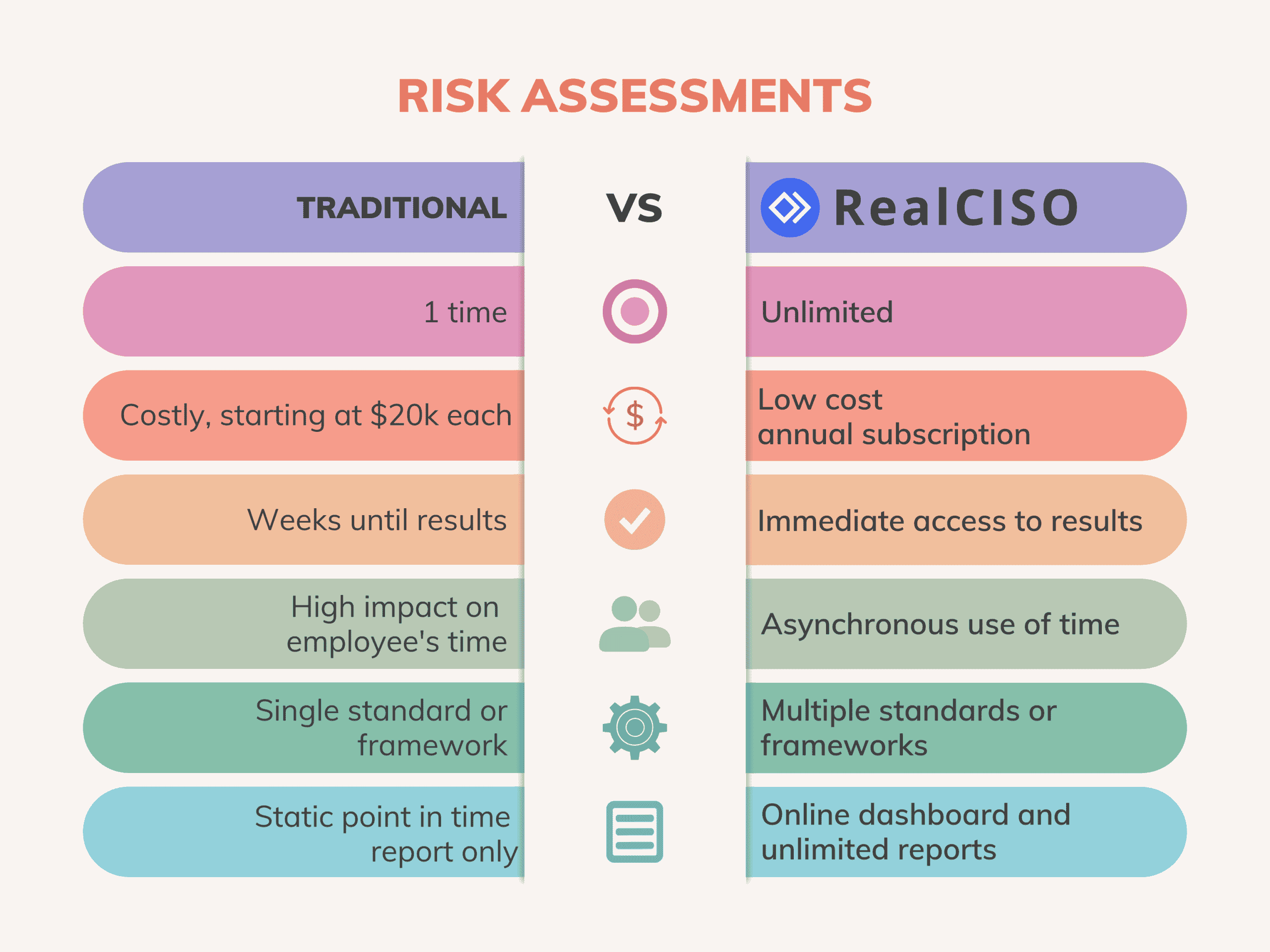
Traditional Risk Assessments vs A Purpose Built SaaS Platform
Organizations are constantly confronted with the challenge of safeguarding their digital assets against an array of threats. This necessitates a robust approach to risk assessment, traditionally fulfilled through consultant-led evaluations. However, the advent of specialized Software as a Service (SaaS) platforms, exemplified by solutions like RealCISO.io, marks a significant shift in how businesses can address these challenges more effectively and efficiently.
This article contrasts traditional risk assessments with the advantages offered by a purpose-built SaaS platform, shedding light on the operational and strategic benefits of the latter.
Traditional Risk Assessments
Traditionally, risk assessments in cybersecurity have been predominantly consultant-led endeavors. These processes are characterized by their intensive demands on time, often stretching over prolonged periods due to the necessity of scheduling meetings, coordinating with multiple stakeholders for information and evidence gathering, and the sequential nature of the tasks involved. The time from the initiation to the conclusion of such assessments can be substantial, leading to delays in implementing critical security measures.
Moreover, traditional cybersecurity assessments are typically point-in-time analyses. They offer a snapshot of an organization’s security posture at a specific moment, without the provision for continuous reassessment. This is a critical limitation, especially considering the dynamic nature of cyber threats and the ongoing changes within an organization’s IT environment. After implementing recommended remediations, organizations often lack the means to reassess their posture without incurring additional costs or undertaking another full-scale assessment.
Financial Impacts
The financial implications of consultant-led risk assessments are another significant consideration. Costs can start from around $20,000 and may escalate to over $100,000 for larger organizations. This investment pertains to a single assessment, with no provision for follow-up evaluations to gauge the effectiveness of implemented remediations. This aspect alone makes traditional assessments a less viable option for many organizations, especially those with limited budgets or those requiring frequent reassessments due to the nature of their operations or industry regulations.
Furthermore, the timeline for obtaining initial results from traditional assessments can be another point of contention. The delay in receiving actionable insights can dissipate the momentum and focus of involved teams, undermining the overall urgency and importance attributed to the cybersecurity measures under consideration.
Additionally, traditional risk assessments typically align with a single standard or framework, limiting their scope. Organizations today, however, often need to comply with multiple regulatory requirements and would benefit from a comprehensive assessment that simultaneously evaluates their compliance against various frameworks. This not only streamlines the assessment process but also provides a more holistic view of an organization’s cybersecurity readiness.
Purpose-built SaaS Platforms
Contrastingly, purpose-built SaaS platforms like RealCISO.io are designed to address these challenges head-on. These platforms offer a streamlined, efficient approach to cybersecurity risk assessments, significantly reducing the time and resources required. They enable continuous risk monitoring and assessments, allowing organizations to quickly gauge the effectiveness of their remediation efforts and adjust their strategies in real-time. Financially, they represent a more cost-effective solution, eliminating the need for expensive consultant-led assessments and offering the flexibility to reassess security postures as needed without additional costs.
Moreover, SaaS platforms provide the agility to assess compliance against multiple standards simultaneously, offering a comprehensive understanding of an organization’s cybersecurity strengths and vulnerabilities. This multi-framework capability facilitates a more strategic approach to cybersecurity, ensuring organizations are not only compliant but also resilient against a broad spectrum of threats.
Conclusion
In conclusion, while traditional risk assessments have played a crucial role in cybersecurity, the dynamic nature of cyber threats and the evolving regulatory landscape necessitate more flexible, efficient, and cost-effective solutions. Purpose-built SaaS platforms like RealCISO.io represent a significant advancement in this domain, offering organizations the tools they need to navigate the complexities of cybersecurity with greater agility and confidence.
The post Traditional Risk Assessments vs A Purpose Built SaaS Platform appeared first on RealCISO.
Roadmap for MSPs and MSSPs to Offer vCISO Services
In an era where cybersecurity threats evolve at an unprecedented pace, businesses, especially small and medium-sized enterprises (SMBs) and small and medium-sized enterprises (SMEs), are increasingly reliant on managed service providers (MSPs) and managed security service providers (MSSPs) for robust cybersecurity defense mechanisms. Virtual Chief Information Security Officer (vCISO) services have emerged as a pivotal offering, bridging the gap between the soaring demand for cybersecurity expertise and the practical constraints of cost and accessibility.
This article offers MSPs and MSSPs a comprehensive roadmap to navigate the complexities of offering vCISO services, highlighting the hidden costs, the indispensable role of automation, and illustrating the return on investment (ROI) through examples. The ultimate goal is to lay down a strategic pathway for service providers to amplify their profitability while delivering exceptional cybersecurity guidance and support.
Understanding the Landscape
Before delving into the intricacies of offering vCISO services, it’s crucial to grasp the strategic importance of such offerings. vCISO services not only plug the cybersecurity expertise gap for SMBs and SMEs but also offer MSPs and MSSPs a golden opportunity to enhance their service portfolio and drive revenue growth. However, the road to successful implementation is fraught with challenges and hidden costs that can impact profitability if not managed adeptly.
The Hidden Costs of vCISO Services
The first step toward a successful vCISO service offering is understanding and managing the hidden costs:
- Salaries and Benefits: The crux of vCISO services lies in the expertise of the professionals. Given the scarcity of skilled cybersecurity experts, attracting top talent requires competitive compensation packages.
- Continuous Training: The cybersecurity landscape is dynamic, with new threats and regulations emerging constantly. Keeping the vCISO team updated necessitates ongoing training and certifications, which incurs significant costs.
- Tools and Technologies: Effective vCISO service delivery hinges on the utilization of advanced tools for risk assessment, policy creation, and compliance management. These tools often come with hefty licensing fees.
- Operational Expenses: From office space to utilities and insurance, the overhead costs of expanding your team and service offerings can accumulate quickly.
- Manual Tasks: Manual, repetitive tasks can consume an inordinate amount of time, detracting from the time available for strategic, high-value activities.
Embracing Automation: A Cost-Cutting Imperative
Automation emerges as a potent tool to mitigate the hidden costs associated with vCISO services. By automating repetitive and time-consuming tasks, MSPs and MSSPs can significantly reduce labor costs and enhance service delivery efficiency. Let’s explore how automation can reshape the vCISO service landscape:
- Reduced Time on Manual Tasks: Automation platforms can drastically cut down the time required for tasks such as security policy creation, risk assessments, and report generation. For instance, what takes 20 hours manually can be reduced to mere minutes with the right automation tool.
- Enhanced Productivity: By automating routine tasks, vCISO professionals can focus on strategic initiatives and high-value client interactions, thereby enhancing overall productivity and service quality.
ROI: Concrete Examples from the Field
The ROI of incorporating automation into vCISO services can be compelling. Consider the following examples:
- Security Report Generation: Manually generating a security report might take 8-15 hours. With an automated vCISO platform like RealCISO, this can be reduced to minutes, yielding a significant saving per report.
- Risk Assessment: Manual risk assessments can take up to 80 hours. Automation can streamline this process to just 2-4 hours, saving hours per assessment.
These examples underscore the tangible benefits of automation, not just in time savings but also in enabling MSPs and MSSPs to reallocate resources towards more strategic and profitable endeavors.
Laying Out a Strategic Pathway
To harness the full potential of vCISO services and achieve sustainable profitability, MSPs and MSSPs should consider the following strategic steps:
- Comprehensive Cost Analysis: Begin with a thorough analysis of all potential costs associated with offering vCISO services, including hidden and indirect expenses.
- Strategic Investment in Automation: Identify areas within the vCISO service delivery process that are ripe for automation. Invest in platforms that offer the best balance of cost savings, efficiency gains, and service quality enhancements.
- Talent Management and Development: Develop a strategic approach to talent acquisition and retention, focusing on competitive compensation, continuous training, and career development opportunities.
- Operational Efficiency: Streamline operational processes to reduce overhead costs, possibly by adopting a hybrid work model to save on office space and utilizing cloud technologies to minimize IT infrastructure expenses.
- Marketing and Client Acquisition: Invest in targeted marketing strategies to promote your vCISO services, emphasizing the value proposition and competitive advantages offered by your automation-enhanced service delivery model.
- Continuous Improvement and Adaptation: Stay abreast of the latest trends in cybersecurity, regulatory changes, and technological advancements. Continuously refine your vCISO service offerings to maintain relevance and competitiveness.
Conclusion
Offering vCISO services represents a significant opportunity for MSPs and MSSPs to expand their service portfolio, drive revenue growth, and address a critical market need. However, success in this endeavor requires careful navigation of the associated complexities, particularly the hidden costs and operational challenges. By strategically embracing automation, MSPs and MSSPs can enhance their service efficiency, cut costs, and improve profitability.
The key lies in a strategic approach that encompasses cost management, automation, talent development, operational efficiency, and continuous improvement. With the right strategies in place, offering vCISO services can become a cornerstone of growth and success in the ever-evolving cybersecurity landscape.
Scale Efficiently with RealCISO
Elevate your cybersecurity offerings and streamline your operations with RealCISO. Discover how our automated vCISO platform can transform your MSP/MSSP business.
Try RealCISO now and lead the way in cybersecurity excellence.
The post Offering vCISO Services: A Roadmap for MSPs and MSSPs appeared first on RealCISO.
HIPAA Compliance
It’s no secret that HIPAA compliance can be a complicated – and expensive – endeavor, even for experienced healthcare industry professionals. But it doesn’t have to be overwhelming! If you’re in healthcare and responsible for HIPAA security, compliance, or cybersecurity in general and are looking to get up-to-speed on the basics of HIPAA and establish your organization as compliant with regulatory standards, this blog post is for you. We’ll cut through the red tape and break down exactly what steps need to be taken so that you can breathe easier knowing your foundation for HIPAA security is in place.
HIPAA Compliance Explained
HIPAA Compliance involves adhering to regulations set by the Health Insurance Portability and Accountability Act. It ensures the protection of patient data. Key elements include: administrative safeguards, physical safeguards, technical safeguards, organizational standards, and policies, procedures, and documentation requirements.
When it comes to HIPAA compliance and other compliance efforts, keeping your organization defensible is key. A great way to do this? Documenting not just what you plan on doing in the future, but what you are actually doing today – something we all should keep in mind! I’ve seen this theory fail plenty of times with hundreds of organizations over the years, so let’s make sure that won’t be us!
Step One: Assess
Assessing your HIPAA compliance is one of the most important steps in keeping your business compliant. It’s a great way to identify any shortfalls, so don’t overlook it! HHS has a self-assessment tool and we at RealCISO offer our free assessment platform that looks not only at the HIPAA Security Rule but other compliances such as SOC2 or PCI-DSS.
Make sure you do an annual checkup (at least!) – this will ensure you have the all-clear status OR know exactly what actionable recommendations are needed to get up-to-speed with regulations.
Step Two: Report
While this might seem like a silly step two, most of us in the security industry have learned and come to agree that to make a program work, we can do it alone. The power of this step, when done correctly, is that we get to the latitude and support needed for step three. When you can present a clear set of shortcomings, with a clear and achievable set of corrective action items, it helps to turn the tides of no into go. The easiest item to resolve if you don’t already have it covered is to create HIPAA security policies.
It’s best general practice in information security to not have a different set of documents for every compliance program, so if you already have documentation built, try your best to work the requirements into those so there is less to manage over time. If however, you find it best for your organization to have a specific set of HIPAA security policies, make sure to keep them accessible to the staff and updated each year or, as they say, upon significant change.
Step Three: Remediate
This is a little chicken or egg, and also a bit of a broken record from above, but now we must get to DOING what we said is being done in our documentation above. In most cases, this should be to continue doing what you are already doing, since that’s what should be documented… However, if on the off chance we chose to say we are doing something in our documentation that is currently in place, make it so in short order. There are a lot of low to no-cost tools that can support a growing cybersecurity program for many size organizations, many of which we have in the RealCISO marketplace.
The reality for healthcare providers – You have so many moving parts within your facility or facilities, all with different protocols often already in place. From ICUs that many times prevent random people from walking through to emergency rooms that can be off-the-chart chaotic on Thanksgiving night when you are highly short-staffed. Keeping your HIPAA security program as simple as possible while still meeting the minimum set of standards should be the target until you have a chance to come up for air and get fancy with your cyber program. Maintaining the delicate balance of protecting ePHI while still being able to provide the care you need for your patients is truly the hardest part of this whole game.
Conclusion
So there you have it! Three actionable steps – Assess, Report, Remediate – to help you build a HIPAA security program and keep it running smoothly. You don’t need to be a security expert, spend an endless amount of money or time, or lose sleep night after night; just following these simple steps will put you on the right track. And if you ever feel like you need a little extra help, RealCISO and all of our partners are here to support you. Our platform has the tools and service connections to get your HIPAA compliance journey started quickly and easily.
So what are you waiting for? Get started today!
The post HIPAA Compliance 101: What Must Be Done appeared first on RealCISO.
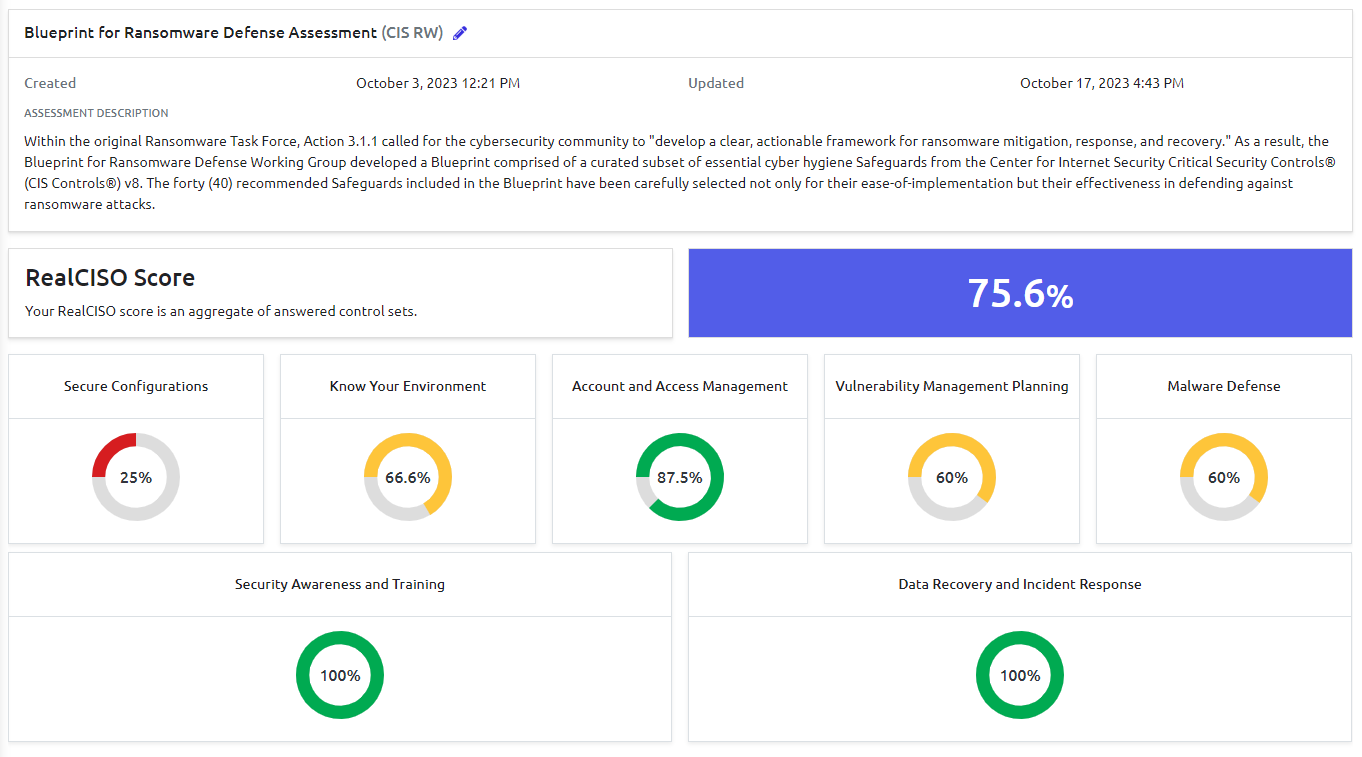
Ransomware Readiness Assessment
The free CIS Ransomware Readiness Assessment is an important tool for businesses and organizations looking to protect themselves from the devastating consequences of a ransomware attack. Ransomware is a type of malicious software that encrypts a victim’s files, making them inaccessible until a ransom is paid to the attackers. It can be a costly and disruptive event, with many organizations losing valuable data, experiencing downtime, and potentially facing legal and regulatory consequences.
“Essential cyber hygiene is the foundation for any good cybersecurity program and removes a critical barrier for small and medium enterprises with limited cyber expertise in defending against ransomware,” said Curtis Dukes, CIS Executive Vice President and General Manager, Security Best Practices.
Center for Internet Security
CIS, or the Center for Internet Security, is a nonprofit organization that works to improve cybersecurity and provide resources and best practices to help businesses and organizations protect themselves from cyber threats. The CIS Ransomware Readiness Assessment is a self-assessment tool designed to help organizations assess their preparedness for ransomware attacks and identify areas for improvement.
Now available free in RealCISO.io, using the CIS Ransomware Readiness Assessment, organizations can evaluate their current cybersecurity practices and identify any weaknesses that could make them vulnerable to ransomware attacks. This includes assessing their backups and disaster recovery processes, network security and access controls, and employee training and awareness.
Key Benefits of the Ransomware Readiness Assessment
One of the key benefits of the CIS Ransomware Readiness Assessment is that it helps organizations identify and prioritize their areas of greatest risk. By identifying their vulnerabilities, organizations can take steps to strengthen their defenses and reduce their risk of a ransomware attack.
In addition to identifying areas of weakness, the CIS Ransomware Readiness Assessment also provides recommendations for improving cybersecurity practices. These recommendations can include implementing stronger passwords and two-factor authentication, regularly updating software and security patches, and providing employee training on how to identify and prevent ransomware attacks.
Importance
The importance of the CIS Ransomware Readiness Assessment cannot be overstated, particularly in today’s increasingly connected and digitized world. Ransomware attacks are becoming more sophisticated and widespread, and it is essential for organizations to take proactive steps to protect themselves.
By using this, organizations can ensure that they are well-prepared to handle a ransomware attack should one occur. This includes having robust backups in place, as well as a plan for responding to and recovering from an attack.
In addition to the financial and operational costs of a ransomware attack, there is also the risk of reputational damage. A ransomware attack can significantly damage an organization’s reputation, leading to lost customers and reduced trust. By taking steps to protect against ransomware attacks, organizations can safeguard their reputation and maintain the trust of their customers and stakeholders.
Summary
In summary, the CIS Ransomware Readiness Assessment is a valuable tool for any organization looking to protect itself from the consequences of a ransomware attack. By identifying vulnerabilities and implementing best practices, organizations can significantly reduce their risk of a ransomware attack and be better prepared to handle one should it occur.
Start today with the Ransomware Readiness Assessment for free in RealCISO
The post Ransomware Readiness Assessment appeared first on RealCISO.
Finding the Right vCISO Software
Virtual Chief Information Security Officer (vCISO) software is an innovative solution that provides businesses with the expertise and guidance of a CISO, without the need for a full-time, in-house professional. This technology-driven approach to information security management is becoming increasingly popular, especially among small to medium-sized businesses (SMBs) that may not have the resources to hire a dedicated CISO.
But what exactly is vCISO software, how does it work, and what benefits can it bring to your organization? Let’s delve deeper into this topic and explore the various aspects of vCISO software.
The Concept of vCISO Software
vCISO software is a service provided by cybersecurity firms that combines the use of advanced tools with the expertise of seasoned cybersecurity professionals. The software component of the service typically includes a suite of tools designed to monitor, manage, and mitigate cybersecurity risks.
On the other hand, the human element of the service involves a team of cybersecurity experts who oversee the software’s operation, interpret its findings, and provide strategic guidance on how to improve the organization’s cybersecurity posture.
How vCISO Software Works
vCISO software works by continuously monitoring an organization’s IT infrastructure for potential security threats. It uses advanced algorithms and machine learning techniques to identify unusual activity that could indicate a cybersecurity breach.
Once a potential threat is detected, the software alerts the team, who then investigates the issue and determines the appropriate response. This could involve anything from patching a software vulnerability to implementing a new security policy.
Benefits of vCISO Software
One of the main benefits of vCISO software is that it provides SMBs with access to high-level cybersecurity expertise at a fraction of the cost of hiring a full-time CISO. This can be particularly beneficial for businesses that lack the resources to maintain a dedicated in-house cybersecurity team.
Additionally, this can help organizations stay ahead of the ever-evolving cybersecurity landscape. The software’s continuous monitoring capabilities, combined with the expertise of the vCISO team, can enable businesses to proactively address security threats before they can cause significant damage.
Selecting the Right vCISO Software
Choosing the right vCISO software for your organization can be a complex task, as there are many factors to consider. Here are some key points to keep in mind during the selection process.
Understanding Your Organization’s Needs
The first step in selecting vCISO software is to understand your organization’s specific needs. This involves identifying your key cybersecurity risks, your existing security infrastructure, and the level of expertise within your team.
Once you have a clear understanding of your needs, you can begin to evaluate different vCISO software options to see which ones align best with your requirements.
Assessing the Software’s Capabilities
When evaluating vCISO software, it’s important to assess the software’s capabilities in relation to your needs. This includes its ability to monitor your IT infrastructure, detect security threats, and provide actionable insights.
It’s also worth considering the software’s ease of use, as this can have a significant impact on its effectiveness. A user-friendly interface and intuitive features can make it easier for your team to leverage the software’s capabilities.
Considering the Provider’s Expertise
Finally, it’s essential to consider the expertise of the vCISO service provider. This includes their experience in the cybersecurity field, their understanding of your industry, and their ability to provide strategic guidance.
A provider with a strong track record in cybersecurity can offer valuable insights and recommendations, helping you to enhance your organization’s security posture and mitigate potential risks.
Conclusion
vCISO software is a powerful tool that can help organizations enhance their cybersecurity capabilities. By combining advanced software tools with the expertise of seasoned professionals, vCISO services can provide businesses with a cost-effective solution to managing their cybersecurity risks.
However, selecting the right vCISO software requires careful consideration of your organization’s needs, the software’s capabilities, and the provider’s expertise. By taking the time to evaluate these factors, you can ensure that you choose a vCISO solution that aligns with your business objectives and provides the level of security you need.
Take Control of Your Cybersecurity with RealCISO
Ready to transform your organization’s security posture with ease and precision? RealCISO is here to guide you through the complexities of cyber risk management. By simply answering a few questions about your current practices, you’ll receive tailored recommendations to fortify your defenses. Embrace the simplicity and effectiveness of RealCISO to stay ahead of evolving technology, best practices, and industry standards. Don’t let compliance be an uphill battle.
Learn More about how RealCISO can empower your cybersecurity strategy today.
The post Understanding vCISO Software appeared first on RealCISO.
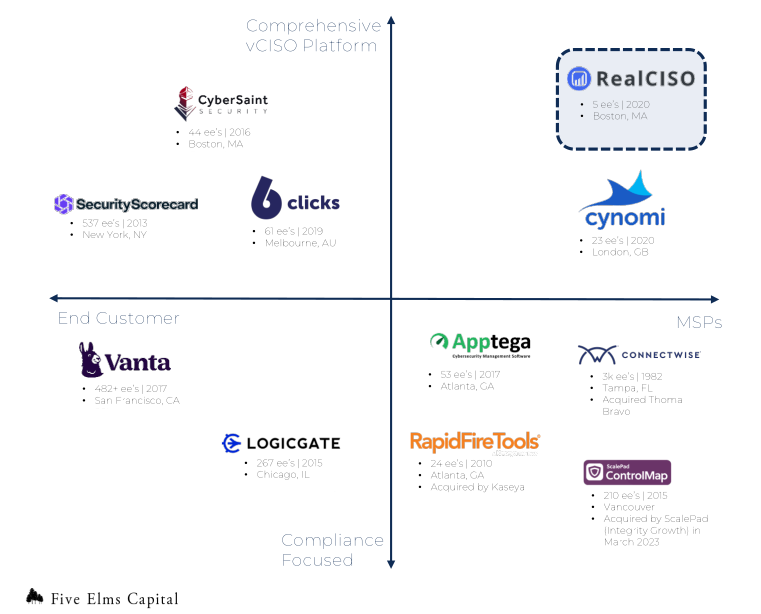
RealCISO is the Market Leader as a vCISO Platform and Software
RealCISO has developed as a robust market leader in a fast-growing market with increasing tailwinds. The product functionality is best-in-class and helps MSPs see immediate ROI as they scale vCISO offerings. The holistic functionality sets itself apart from its MSP-specific peers who index solely on compliance.
vCISO Management Market Analysis
Many MSPs still rely on in-house manual processes that are both time-intensive and inefficient. This limits the number of customers they can serve and limits their insights into upsell opportunities. vCISO management solutions improve operational efficiency and augment revenue opportunities, making ROI immediately tangible.
MSPs Rely on Purpose-Built Software
MSPs cannot use traditional GRC solutions to manage end customers, as these solutions are not purpose-built for an MSP’s unique needs. The majority of these solutions are not multi-tenant and lack unique and personalized content frameworks, service provider insights, and tailor-made remediation plans.
MSPs Require Comprehensive Solutions, Not Solely Compliance-Specific Ones
While there are other MSP-specific players like Apptega, ConnectWise, and ControlMap, these are largely focused on compliance frameworks. While this is an integral component for MSPs, they also need security frameworks and remediation functionality, which is where RealCISO separates itself from its peers.
MSP & vCISO Market Growth
With 40k+ MSPs in the United States and 150k+ MSPs globally, the market opportunity is immense. As more MSPs adopt and expand vCISO offerings, the market demand will only grow. SMBs and mid-market companies continue to seek out cost -efficient ways to improve security posture, which will continue to catalyze the market growth.
Key Takeaways on RealCISO
The vCISO software landscape is populated by solutions that focus on compliance, offering limited functionality beyond regulatory adherence, and is ripe for innovative providers like RealCISO, who are uniquely positioned to lead the way.
RealCISO wins by delivering a nuanced, feature-rich platform that provides a holistic solution to the end customer cyber risk needs while remaining intuitive and easy to use – both of which are the biggest features requested by middle market, vCISOs, MSPs and MSSPs.
RealCISO’s platform drives end customer ROI and allows MSPs to complete tasks in a fraction of the time. Purpose-built modules solve nuanced industry challenges, driving efficiency and a streamlined experience.
Market analysis provided by 5 Elms Capital
Ready to Start with RealCISO
Ready to transform your cybersecurity management? Join the leaders who are already leveraging RealCISO’s innovative platform to drive unparalleled efficiency and ROI. Elevate your MSP offerings with our comprehensive, easy-to-use vCISO solutions. Don’t just meet compliance—exceed it with our holistic approach to cyber risk management. Start your journey to superior cybersecurity today.
Discover the RealCISO difference now!
The post RealCISO’s Market Position is Ideal for MSPs & MSSPs appeared first on RealCISO.
Cynomi Alternatives
In the ever-evolving landscape of cybersecurity, the role of a virtual Chief Information Security Officer (vCISO) has become increasingly important. Businesses of all sizes are recognizing the need for a dedicated professional to oversee their information security strategies. However, hiring a full-time vCISO can be cost-prohibitive for many organizations. This is where Cynomi comes into the picture, offering a virtual CISO service that promises to deliver the same level of expertise and oversight at a fraction of the cost. But what if you’re looking for an alternative to Cynomi? In this comprehensive exploration, we’ll delve into some of the best alternatives available in the market today.
Understanding the Role of a vCISO
The role of a vCISO is to provide strategic leadership in an organization’s cybersecurity efforts. This includes everything from developing and implementing security policies to managing risk and ensuring compliance with relevant regulations. A vCISO is also responsible for educating staff about cybersecurity best practices and responding to security incidents.
However, not all businesses have the resources to hire a full-time vCISO. This is where virtual CISO services come into play. These services provide businesses with access to experienced cybersecurity professionals on an as-needed basis, allowing them to benefit from expert guidance without the hefty price tag of a full-time hire.
Why Look for a Cynomi Alternative?
Cynomi is a popular vCISO platform, known for its comprehensive approach to cybersecurity. However, it may not be the right fit for every business. Some organizations may find Cynomi’s services too expensive, while others may require a more specialized approach to cybersecurity. Additionally, some businesses may simply prefer to work with a different provider due to personal preference or past experiences.
Whatever the reason, it’s important to know that there are Cynomi alternatives out there. These range from other full-service vCISO providers to specialized cybersecurity consultancies. The key is to find a provider that aligns with your business’s specific needs and budget.
Exploring Cynomi Alternatives
1. RealCISO
RealCISO is an established front runner as a platform for vCISOs to use with clients. RealCISO’s focus on providing a broad range of compliance frameworks and its cost-effective approach can be particularly appealing to vCISOs looking to manage cyber risks efficiently without overburdening their own limited resources.
One of the key advantages of RealCISO is it’s a multi-tenant platform that streamlines the provision of vCISO services on a large scale, automating essential components such as risk and compliance assessments, gap analysis, and the development of customized policies. The platform intelligently crafts strategic remediation plans, complete with prioritized tasks, and offers robust tools for ongoing task management and progress monitoring. RealCISO also has a lower price point for vCISOs to use with clients, thus reducing expenses.
2. CyberGRX
CyberGRX is a global leader in third-party cyber risk management. As a Cynomi alternative, CyberGRX offers a range of services, including risk assessments, risk mitigation strategies, and ongoing risk monitoring. Their approach is data-driven, allowing businesses to make informed decisions about their cybersecurity strategies.
One of the key advantages of CyberGRX is its focus on third-party risk. Many businesses overlook the cybersecurity risks associated with their vendors and partners, but these can be just as significant as internal risks. CyberGRX helps businesses identify and manage these risks effectively.
3. Cybereason
Cybereason is another strong Cynomi alternative. This cybersecurity company offers a range of services, including threat hunting, incident response, and risk management. Cybereason’s approach is proactive, with a focus on detecting and responding to threats before they can cause significant damage.
One of the standout features of Cybereason is its AI-driven threat detection. This allows the company to identify and respond to threats more quickly and accurately than traditional methods. For businesses that are particularly concerned about advanced threats, Cybereason could be an excellent choice.
Choosing the Right Cynomi Alternative
Choosing the right Cynomi alternative comes down to understanding your business’s specific needs. Do you need a provider that can help you manage third-party risk? Are you looking for a proactive approach to threat detection? Or do you simply need a reliable vCISO service that can provide strategic guidance?
Once you’ve identified your needs, you can start comparing different providers. Look at their range of services, their approach to cybersecurity, and their reputation in the industry. Don’t be afraid to ask for references or case studies to get a better idea of what they can offer.
Remember, the goal is to find a Cynomi alternative that can provide the same level of expertise and oversight, but in a way that aligns with your business’s unique needs and budget. With the right provider, you can ensure that your business’s cybersecurity is in good hands.
Discover Your Ideal vCISO Solution with RealCISO
Embark on the journey to fortify your cybersecurity without the complexity. RealCISO is your trusted partner, offering a streamlined platform that demystifies the process of enhancing your security posture. By simply answering a few questions, you’ll receive tailored recommendations to close security gaps, ensuring compliance with industry standards like SOC2, HIPAA, CMMC 2.0, and more. Don’t let cyber risk be an uphill battle.
Take the first step towards a more secure future and Learn More about how RealCISO can empower your organization with a proactive, efficient, and effective cybersecurity strategy.
The post Cynomi Alternative for a vCISO appeared first on RealCISO.
Compliance Management with a Cybersecurity Dashboard
Compliance management can be a complex and time-consuming task for businesses. The need for efficient and effective compliance processes is paramount to ensure smooth operations and mitigate risks. This is where a cybersecurity dashboard comes in handy. With its user-friendly interface and comprehensive features, it simplifies compliance management for businesses of all sizes.
Simplify Compliance Management for Your Business
Streamlining compliance processes is crucial for efficient operations. A cybersecurity dashboard provides a centralized platform where businesses can manage various compliance tasks, such as risk assessments, policy enforcement, and incident response. By consolidating these processes, organizations can save time and resources, allowing them to focus on other critical aspects of their operations.
Compliance management is a complex and ever-evolving task for businesses of all sizes. With the increasing number of regulations and standards that organizations need to adhere to, it can be challenging to keep up with the requirements. This is where a cybersecurity dashboard comes in handy. It simplifies the compliance management process by providing a comprehensive view of all compliance-related activities.
One of the key benefits of a cybersecurity dashboard is its ability to streamline compliance processes. It allows businesses to automate repetitive tasks, such as data collection, analysis, and reporting. By eliminating manual work, organizations can allocate their resources more effectively, ensuring compliance without compromising efficiency.
Imagine a scenario where a business has to manually collect data from various sources, analyze it, and generate reports to demonstrate compliance. This process can be time-consuming and prone to errors. However, with a cybersecurity dashboard, all these tasks can be automated. The dashboard can pull data from different systems, perform real-time analysis, and generate comprehensive reports with just a few clicks.
Streamlining Compliance Processes for Efficient Operations
A cybersecurity dashboard not only automates tasks but also provides a centralized platform for managing compliance activities. It acts as a single source of truth, where all compliance-related information is stored and easily accessible. This eliminates the need for businesses to maintain multiple spreadsheets or documents, reducing the risk of data inconsistencies and ensuring that everyone has access to the most up-to-date information.
Furthermore, a cybersecurity dashboard can integrate with other systems, such as ticketing systems or incident response platforms, to streamline incident management. When a compliance breach occurs, the dashboard can automatically create an incident ticket, assign it to the appropriate team members, and track its resolution. This ensures that compliance incidents are addressed promptly and efficiently, minimizing the impact on the business.
Prioritizing Compliance Tasks for Effective Risk Management
A cybersecurity dashboard enables businesses to prioritize compliance tasks based on their risk levels. By analyzing and categorizing risks, organizations can allocate their resources according to the severity of potential consequences. This proactive approach helps prevent compliance breaches and ensures that the most critical tasks are addressed first.
For example, if a risk assessment identifies a high-risk area that requires immediate attention, the cybersecurity dashboard can automatically assign the task to the responsible team members and track its progress. This ensures that no critical compliance tasks fall through the cracks and helps organizations stay ahead of potential risks.
In addition to prioritizing compliance tasks, a cybersecurity dashboard can also provide real-time visibility into the organization’s compliance status. It can generate visual reports and dashboards that show the current state of compliance, highlighting areas that need improvement. This helps businesses identify gaps in their compliance programs and take corrective actions before they become compliance issues.
In conclusion, a cybersecurity dashboard is a powerful tool for simplifying compliance management. It streamlines compliance processes, automates repetitive tasks, and prioritizes compliance tasks based on risk levels. By using a cybersecurity dashboard, businesses can ensure efficient operations, reduce the risk of compliance breaches, and stay ahead of regulatory requirements.
Enhance Supply Chain Compliance Tracking
Managing compliance across complex supply chains can be challenging. With multiple tiers and distinct segments or enclaves involved, keeping track of compliance requirements can become overwhelming. However, a cybersecurity dashboard simplifies this process by providing a comprehensive view of the entire supply chain and ensuring compliance at every level.
Managing Compliance Across Multi-Tier Supply Chains
A cybersecurity dashboard allows businesses to track compliance across multi-tier supply chains. It provides visibility into the compliance status of all suppliers, enabling organizations to identify potential risks and take appropriate actions. By ensuring compliance at every level, businesses can maintain the integrity of their supply chains and safeguard their operations from compliance-related disruptions.
For example, imagine a global electronics manufacturer that sources components from various suppliers located in different countries. Each supplier is responsible for complying with specific regulations and standards. With a cybersecurity dashboard, the manufacturer can easily monitor the compliance status of each supplier, ensuring that they meet the necessary requirements. This proactive approach helps mitigate the risk of non-compliance and potential disruptions in the supply chain.
Furthermore, a cybersecurity dashboard provides real-time updates on compliance metrics, such as the number of suppliers in compliance, the percentage of non-compliant suppliers, and the overall compliance score. This data allows businesses to identify trends and patterns in compliance performance, enabling them to make informed decisions and implement corrective actions when necessary.
Ensuring Compliance in Distinct Segments or Enclaves
In certain industries or business environments, compliance requirements can vary across distinct segments or enclaves. A cybersecurity dashboard provides the flexibility to tailor compliance processes according to these specific requirements. It allows businesses to define separate compliance policies, track their implementation, and ensure adherence to industry-specific regulations.
Take, for instance, the healthcare sector, where compliance with regulations such as the Health Insurance Portability and Accountability Act (HIPAA) is crucial. Within a healthcare organization, there are different departments and units that handle sensitive patient information. Each department may have unique compliance requirements based on their specific roles and responsibilities.
A cybersecurity dashboard enables healthcare organizations to create customized compliance policies for each department and track their implementation. It provides a centralized platform where compliance officers can monitor the adherence to HIPAA regulations, ensuring that all departments handle patient data securely and in compliance with the law. This level of granularity in compliance tracking helps organizations mitigate the risk of data breaches and maintain patient trust.
Moreover, a cybersecurity dashboard can generate detailed compliance reports for each segment or enclave, highlighting areas of improvement and potential vulnerabilities. These reports can be used to initiate targeted training programs, allocate resources effectively, and continuously enhance compliance practices within the organization.
In conclusion, a cybersecurity dashboard is a powerful tool for enhancing supply chain compliance tracking. It enables businesses to manage compliance across multi-tier supply chains, ensuring the integrity of operations and mitigating potential disruptions. Additionally, it allows organizations to tailor compliance processes to distinct segments or enclaves, enabling adherence to industry-specific regulations. By leveraging the capabilities of a cybersecurity dashboard, businesses can strengthen their compliance efforts and establish a robust foundation for secure and compliant supply chain operations.
User-Friendly Tools for Compliance Management
Compliance management should not be limited to security experts. It should also cater to beginners and individuals with limited technical knowledge. A cybersecurity dashboard offers user-friendly tools and features that simplify compliance management for users of all levels of expertise.
Step-by-Step Guidance and Templates for Easy Compliance
A cybersecurity dashboard provides step-by-step guidance and customizable policy templates to facilitate easy compliance. These tools help users understand compliance requirements, implement necessary controls, and generate compliant documentation. The intuitive interface and clear instructions make it easy for even non-technical users to navigate and manage compliance tasks effectively.
Supporting Security Experts and Beginners Alike
A cybersecurity dashboard is designed to support both security experts and beginners in managing compliance. It offers advanced features for experienced professionals, such as advanced reporting and analytics, while also providing simplified options for beginners. This ensures that organizations can leverage the full potential of the dashboard, regardless of their users’ level of expertise.
Introducing the Powerful Cybersecurity Dashboard
The cybersecurity dashboard is a powerful tool that revolutionizes compliance management for businesses. Its comprehensive features, user-friendly interface, and flexibility make it an essential solution for organizations looking to simplify their compliance processes and enhance operational efficiency.
Streamline Cybersecurity Lifecycle Management
A cybersecurity dashboard goes beyond compliance management. It also streamlines the entire lifecycle of cybersecurity practices within an organization. Let’s explore some key benefits of incorporating a cybersecurity dashboard into your risk management strategy.
Seamlessly Transition from NIST 800-171 to CMMC
A cybersecurity dashboard ensures a seamless transition from NIST 800-171 to the Cybersecurity Maturity Model Certification (CMMC). It provides a clear roadmap and actionable steps to achieve compliance with the evolving regulatory landscape. By staying ahead of compliance requirements, organizations can protect their sensitive data and maintain strong cybersecurity postures.
Improve Risk Management with Streamlined Compliance
By integrating compliance management into a cybersecurity dashboard, organizations can improve their overall risk management practices. The dashboard enables businesses to identify potential risks, implement controls, and monitor compliance in real-time. This proactive approach helps reduce vulnerabilities, minimize the impact of cybersecurity incidents, and protect critical assets.
Accelerate Compliance with Customizable Policy Templates
Customizable policy templates are a key feature of a cybersecurity dashboard. They enable organizations to adopt industry best practices and regulatory requirements, without reinventing the wheel. With pre-defined templates, businesses can quickly configure their compliance policies, saving time and ensuring consistency across their operations.
In conclusion, a cybersecurity dashboard simplifies compliance management for businesses of all sizes. It streamlines compliance processes, enhances supply chain compliance tracking, provides user-friendly tools, and supports the entire lifecycle of cybersecurity practices. By leveraging the power of a cybersecurity dashboard, organizations can streamline their compliance processes, improve risk management, and enhance operational efficiency.
The post Simplify Compliance Management with a Cybersecurity Dashboard appeared first on RealCISO.
Cyber Security Dashboard for Board of Directors
As the digital landscape continues to evolve, so does the threat of cyber attacks. For businesses, this means that cyber security is no longer just an IT issue, but a board-level concern. A cyber security dashboard can provide the board of directors with a clear and concise view of the company’s security posture, helping them make informed decisions to protect the business.
Understanding the Importance of Cyber Security
In today’s interconnected world, cyber threats are a constant concern. From data breaches to ransomware attacks, businesses of all sizes are at risk. The consequences of a cyber attack can be devastating, leading to financial losses, damage to reputation, and regulatory penalties.
For the board of directors, understanding the cyber security landscape is crucial. They need to be aware of the threats facing the business, the potential impact of these threats, and the measures in place to mitigate them. This is where a cyber security dashboard comes into play.
The Role of a Cyber Security Dashboard
A cyber security dashboard is a tool that provides a visual representation of a company’s security status. It aggregates data from various sources, presenting it in an easy-to-understand format. This allows the board of directors to quickly assess the company’s security posture and make informed decisions.
The dashboard can include a variety of information, such as the number of detected threats, the status of security controls, and the company’s compliance with relevant regulations. It can also provide insights into trends and patterns, helping the board identify potential areas of concern.
Key Features of a Cyber Security Dashboard
A well-designed cyber security dashboard should be easy to use, providing the board with a clear view of the company’s security status. It should include real-time data, allowing the board to monitor the company’s security posture continuously. The dashboard should also be customizable, enabling the board to focus on the information that is most relevant to them.
Another important feature of a cyber security dashboard is the ability to generate reports. These reports can provide a detailed analysis of the company’s security status, highlighting areas of concern and suggesting potential improvements. This can be particularly useful for the board when making strategic decisions about the company’s security strategy.
Implementing a Cyber Security Dashboard
Implementing a cyber security dashboard involves several steps. First, the company needs to identify the key metrics that the dashboard will track. These metrics should be aligned with the company’s security objectives and should provide a comprehensive view of the company’s security status.
Next, the company needs to select a dashboard tool that meets its needs. This tool should be able to aggregate data from various sources, present it in a clear and concise format, and provide real-time updates. The tool should also be secure, ensuring that the data it contains is protected from unauthorized access.
Training and Support
Once the dashboard is implemented, it’s important to provide training and support to the board of directors. They need to understand how to use the dashboard, what the data means, and how to interpret it. This can be achieved through training sessions, user guides, and ongoing support from the IT team.
In addition, the company should regularly review and update the dashboard to ensure it remains relevant and useful. This includes updating the metrics as the company’s security objectives change, adding new data sources, and making improvements based on user feedback.
Conclusion
A cyber security dashboard is a valuable tool for the board of directors. It provides a clear and concise view of the company’s security status, helping the board make informed decisions to protect the business. By understanding the importance of cyber security, implementing a dashboard, and providing ongoing training and support, companies can enhance their security posture and mitigate the risk of cyber threats.
Empower Your Cyber Security Strategy with RealCISO
Ready to elevate your board’s oversight on cyber security? RealCISO is here to transform the way you manage your organization’s security posture. With our intuitive platform, you can quickly understand and address cyber risks, ensuring compliance with industry standards and best practices. Don’t let the complexity of cyber threats slow you down.
Take the first step towards a more secure future by exploring how RealCISO can make cyber security management simple, fast, and effective.
Learn More about how RealCISO can guide you to a stronger security posture with actionable insights.
The post Cyber Security Dashboard for Board of Directors appeared first on RealCISO.
Understanding Cyber Security Dashboards
Cyber security dashboards are essential tools in the modern digital landscape. They provide a comprehensive overview of an organization’s security posture, enabling IT professionals to monitor, analyze, and respond to potential threats in real time. This article delves into the intricacies of these dashboards, their importance, and how they can be effectively utilized.
The Concept of Cyber Security Dashboards
A cyber security dashboard is a visual interface that displays an organization’s security metrics in an easy-to-understand format. It aggregates data from various sources, providing a holistic view of the network’s security status. The dashboard aids in identifying vulnerabilities, detecting anomalies, and tracking the effectiveness of security measures.
These dashboards are customizable, allowing organizations to focus on metrics that are most relevant to their operations. They can be tailored to display information such as the number of attempted breaches, detected malware, or patching status of systems.
Importance of Cyber Security Dashboards
In today’s interconnected world, cyber threats are evolving at an alarming rate. Organizations need to stay ahead of these threats to protect their sensitive data. This is where cyber security dashboards come into play.
Firstly, these dashboards provide real-time visibility into the organization’s security posture. This enables the IT team to detect and respond to threats promptly, reducing the potential damage.
Secondly, they simplify the complex data associated with cyber security. By presenting data in a visual format, dashboards make it easier for IT professionals to understand and interpret the information, leading to quicker decision-making.
Lastly, dashboards aid in compliance. Many industries have regulations requiring businesses to monitor and report on their security status. Dashboards can generate these reports, making it easier for organizations to meet their regulatory obligations.
Key Components of a Cyber Security Dashboard
Threat Intelligence
Threat intelligence is a crucial component of a cyber security dashboard. It involves gathering and analyzing information about potential or current attacks that threaten an organization. The dashboard should display this information in a way that allows for quick identification of threats and immediate action.
Threat intelligence can come from various sources, including internal data, threat feeds, and open-source intelligence. The dashboard should be capable of integrating this data to provide a comprehensive view of the threat landscape.
Incident Response
Incident response is another key component. The dashboard should provide information about the status of ongoing incident responses, including the nature of the incident, the systems affected, and the steps taken to mitigate it.
Moreover, it should allow for easy communication between team members. This can be achieved through features like chat windows or integration with communication platforms.
Risk Assessment
Risk assessment involves identifying, evaluating, and prioritizing risks. The dashboard should display the identified risks, their potential impact, and the measures taken to mitigate them. This helps organizations focus their resources on the most significant threats.
Furthermore, the dashboard should allow for easy updating of risk assessments as new information becomes available. This ensures that the organization’s risk profile is always up to date.
Choosing the Right Cyber Security Dashboard
With the plethora of cyber security dashboards available in the market, choosing the right one can be a daunting task. However, by focusing on certain key factors, organizations can make an informed choice.
Firstly, the dashboard should be easy to use. It should have a user-friendly interface that allows for easy navigation and customization. It should also be capable of integrating with the organization’s existing systems.
Secondly, the dashboard should provide real-time updates. In the fast-paced world of cyber security, having access to real-time data is crucial. The dashboard should be able to pull data from various sources and update the display in real time.
Lastly, the dashboard should have robust reporting capabilities. It should be able to generate detailed reports that can be used for compliance purposes or for presenting to management.
In conclusion, a cyber security dashboard is an invaluable tool in the fight against cyber threats. By providing a comprehensive view of an organization’s security posture, it enables IT professionals to monitor, analyze, and respond to potential threats effectively. However, choosing the right dashboard requires careful consideration of the organization’s specific needs and the features offered by the dashboard.
Take Control of Your Cyber Security with RealCISO
Ready to elevate your organization’s security posture with a solution that’s both powerful and user-friendly? RealCISO is here to guide you through the complexities of cyber risk management. By answering a few straightforward questions, you’ll gain actionable insights to fortify your defenses and stay ahead of evolving threats.
With RealCISO, compliance with frameworks like SOC2, HIPAA, CMMC 2.0, NIST 800-171, and more becomes a streamlined process, allowing you to focus on what matters most. Don’t let cyber risk management be an uphill battle.
Learn More about how RealCISO can transform your cyber security strategy today.
The post Understanding Cyber Security Dashboards appeared first on RealCISO.
Understanding the Cyber Dashboard
The cyber dashboard is an essential tool for managing and monitoring cyber security in today’s digital world. It provides a comprehensive overview of an organization’s cyber security status, helping to identify potential threats and vulnerabilities. This article will delve into the various aspects of a cyber dashboard, its importance, and how it can be effectively utilized.
The Importance of a Cyber Dashboard
A cyber dashboard is not just a fancy tool for tech enthusiasts. It is a crucial component of any organization’s cyber security strategy. It provides real-time data about the organization’s security posture, helping to detect and respond to threats promptly.
Moreover, a cyber dashboard simplifies the complex task of managing cyber security. It presents information in a user-friendly format, making it easier for non-technical staff to understand and act upon. This democratization of data is crucial in ensuring that everyone in an organization understands the importance of cyber security and their role in maintaining it.
Key Features of a Cyber Dashboard
A cyber dashboard is not a one-size-fits-all solution. It can be customized to meet the specific needs of an organization. However, there are certain key features that every cyber dashboard should have.
Firstly, it should provide real-time monitoring and alerts. This ensures that any potential threats are identified and dealt with promptly. Secondly, it should have a user-friendly interface. This makes it easier for non-technical staff to understand and use the dashboard effectively. Finally, it should provide comprehensive reports. These reports can be used to analyze trends and identify areas for improvement.
Real-Time Monitoring and Alerts
One of the most important features of a cyber dashboard is its ability to provide real-time monitoring and alerts. This means that the dashboard is constantly scanning the organization’s network for any potential threats or vulnerabilities. If anything suspicious is detected, the dashboard will alert the relevant personnel so that they can take immediate action.
This feature is crucial in today’s fast-paced digital world, where cyber threats can emerge and evolve in a matter of minutes. By providing real-time monitoring and alerts, a cyber dashboard ensures that an organization is always one step ahead of the cyber criminals.
User-Friendly Interface
A cyber dashboard should not only be powerful, but also easy to use. It should have a user-friendly interface that makes it easy for non-technical staff to understand and use the dashboard effectively. This includes clear and concise data visualizations, intuitive navigation, and easy-to-understand terminology.
Moreover, a user-friendly interface can help to foster a culture of cyber security within an organization. If everyone can understand and use the dashboard, they are more likely to take cyber security seriously and play their part in maintaining it.
Comprehensive Reports
Finally, a cyber dashboard should provide comprehensive reports. These reports should provide detailed information about the organization’s cyber security status, including any threats or vulnerabilities that have been detected, the actions that have been taken to address them, and the results of these actions.
These reports can be used to analyze trends, identify areas for improvement, and demonstrate compliance with cyber security regulations. They can also be used to communicate the organization’s cyber security status to stakeholders, such as customers, investors, and regulators.
Implementing a Cyber Dashboard
Implementing a cyber dashboard can be a complex task, but it is well worth the effort. It requires careful planning, a clear understanding of the organization’s cyber security needs, and a commitment to ongoing maintenance and improvement.
The first step in implementing a cyber dashboard is to identify the organization’s cyber security needs. This includes identifying the types of threats and vulnerabilities that the organization is most likely to face, the data that needs to be monitored, and the personnel who will be using the dashboard.
Next, the organization needs to choose a cyber dashboard that meets these needs. This includes evaluating the dashboard’s features, ease of use, and compatibility with the organization’s existing systems. Once the dashboard has been chosen, it needs to be customized to fit the organization’s needs and then deployed across the organization.
Finally, the organization needs to train its personnel on how to use the dashboard effectively. This includes providing training on how to interpret the data, how to respond to alerts, and how to generate and analyze reports.
Conclusion
In conclusion, a cyber dashboard is an essential tool for managing and monitoring cyber security in today’s digital world. It provides a comprehensive overview of an organization’s cyber security status, helping to identify potential threats and vulnerabilities. By implementing a cyber dashboard, an organization can enhance its cyber security, protect its valuable data, and stay one step ahead of the cyber criminals.
Take Control of Your Cyber Security with RealCISO
Ready to elevate your organization’s cyber security and simplify the process of managing cyber risks? RealCISO is your trusted guide in the ever-evolving landscape of cyber security. By answering a few straightforward questions, you can gain actionable insights and recommendations tailored to your organization’s unique needs. Whether you’re navigating compliance frameworks like SOC2, HIPAA, CMMC 2.0, NIST 800-171, or aiming to align with the NIST Cybersecurity Framework, RealCISO makes it simple, fast, and effective. Don’t let cyber threats dictate your security posture.
Learn More about how RealCISO can help you stay ahead in the digital world.
The post Understanding the Cyber Dashboard appeared first on RealCISO.
The Cybersecurity Dashboard
The cybersecurity dashboard is a crucial tool for organizations to monitor, assess, and respond to security threats. It provides a comprehensive view of an organization’s security posture, offering real-time insights into potential vulnerabilities and ongoing attacks. This article delves into the intricacies of a cybersecurity dashboard, its importance, features, and how to effectively use it.
Importance of a Cybersecurity Dashboard
In the digital age, cybersecurity threats are a constant concern for businesses of all sizes. A breach can lead to significant financial losses, damage to reputation, and potential legal repercussions. Therefore, having a robust cybersecurity strategy is paramount, and a cybersecurity dashboard is a key component of this strategy.
A cybersecurity dashboard provides a centralized view of an organization’s security landscape. It aggregates data from various sources, presenting it in an easy-to-understand format. This allows for quick identification of threats, enabling swift action to mitigate potential damage.
Real-Time Threat Detection
The ability to detect threats in real-time is a critical feature of a cybersecurity dashboard. It continuously monitors network traffic, identifying anomalies that may indicate a potential attack. This allows for immediate response, reducing the likelihood of a successful breach.
Real-time threat detection also provides valuable data for future threat prevention. By analyzing the nature of detected threats, organizations can refine their security protocols and enhance their defenses against similar attacks in the future.
Cybersecurity Dashboard Compliance Reporting
Many industries have strict regulations regarding data security. A dashboard can help organizations maintain compliance with these regulations. It provides detailed reports on security measures, breaches, and responses, which can be used to demonstrate compliance during audits.
Additionally, these reports can be used internally to assess the effectiveness of current security measures and identify areas for improvement. This proactive approach to security management can significantly reduce the risk of a breach.
Key Features of a Cybersecurity Dashboard
A well-designed dashboard should provide a comprehensive overview of an organization’s security landscape. It should be intuitive, easy to navigate, and customizable to meet the specific needs of the organization.
While the exact features will vary depending on the specific dashboard, there are several key features that should be included in any effective cybersecurity dashboard.
Threat Intelligence
Threat intelligence is a crucial feature of a dashboard. It involves collecting and analyzing data from various sources to identify potential threats. This information is then used to inform security measures and response strategies.
The best cybersecurity dashboards provide real-time threat intelligence, allowing for immediate response to detected threats. They also offer predictive threat intelligence, using historical data to predict future threats and prepare accordingly.
Incident Response Management
When a threat is detected, swift and effective response is crucial. A cybersecurity dashboard should include features for incident response management, such as automated alerts, incident tracking, and response coordination tools.
These features enable organizations to quickly respond to threats, minimizing potential damage and downtime. They also provide valuable data for post-incident analysis, which can be used to improve future response strategies.
Effectively Using a Cybersecurity Dashboard
Simply having a cybersecurity dashboard is not enough. To truly benefit from this tool, organizations must know how to use it effectively.
This involves understanding the dashboard’s features, customizing it to meet the organization’s needs, and integrating it into the overall cybersecurity strategy.
Customization
Every organization has unique security needs. Therefore, a one-size-fits-all dashboard is unlikely to be effective. The best cybersecurity dashboards allow for extensive customization, enabling organizations to focus on the threats that are most relevant to them.
This might involve customizing the types of data displayed, the layout of the dashboard, or the alerts and notifications. By tailoring the dashboard to their specific needs, organizations can ensure that they are getting the most out of this tool.
Integration
A cybersecurity dashboard should not be used in isolation. Instead, it should be integrated into the overall cybersecurity strategy. This means using the data and insights provided by the dashboard to inform security measures, response strategies, and ongoing security management.
By integrating the cybersecurity dashboard into the larger security strategy, organizations can ensure that they are taking a proactive, data-driven approach to cybersecurity.
Conclusion
A cybersecurity dashboard is a powerful tool for managing and enhancing an organization’s security posture. By providing real-time threat detection, compliance reporting, and a range of other features, it enables organizations to respond swiftly to threats, maintain compliance, and continuously improve their security measures.
However, to truly benefit from a cybersecurity dashboard, organizations must understand how to use it effectively. This involves customizing the dashboard to meet their specific needs and integrating it into their overall cybersecurity strategy.
With a well-designed and effectively used cybersecurity dashboard, organizations can significantly enhance their security posture, reducing the risk of a breach and the potential damage that can result.
Take Control of Your Cybersecurity Posture with RealCISO
Ready to elevate your organization’s security measures with actionable insights and tailored recommendations? Discover how RealCISO can transform your cybersecurity strategy with just a few clicks. By answering simple questions about your current practices, you’ll receive a clear roadmap to close security gaps and align with industry standards like SOC2, HIPAA, CMMC 2.0, and more. Don’t let the complexity of cyber risk management hold you back.
Learn More about how RealCISO can guide you to a stronger, more resilient security posture.
The post Understanding the Cybersecurity Dashboard appeared first on RealCISO.
In today’s fast-paced and ever-evolving business landscape, organizations are faced with numerous challenges when it comes to maintaining compliance and managing risk. Governance, Risk, & Compliance (GRC) has become a critical aspect of business operations, ensuring that organizations adhere to various industry-specific regulations and standards. To navigate the complex world of GRC, businesses need a comprehensive solution that not only streamlines compliance efforts but also enhances overall risk management. RealCISO, a pioneering platform, offers exactly that – a holistic approach to GRC that empowers organizations to come full circle in their compliance journey.
Understanding the Importance of GRC in Today’s Business Landscape
Before delving into RealCISO’s role in strengthening compliance efforts, it is crucial to understand the significance of GRC in today’s business environment. With the ever-increasing number of industry regulations and cyber threats, organizations need to prioritize compliance to protect sensitive data and maintain customer trust. GRC encompasses a wide range of activities, including risk management, internal controls, audits, and reporting. By adopting a proactive approach to GRC, businesses can identify potential risks, mitigate them effectively, and ensure that objectives are achieved while maintaining compliance.
In today’s interconnected world, where information is exchanged at lightning speed, businesses face numerous challenges when it comes to managing risk and compliance. The digital landscape has opened up new avenues for cybercriminals, making it essential for organizations to have robust GRC frameworks in place. These frameworks help businesses navigate the complex regulatory landscape, ensuring that they meet all the necessary requirements and avoid costly penalties.
One of the key aspects of GRC is risk management. By identifying and assessing potential risks, businesses can take proactive measures to mitigate them. This involves conducting thorough risk assessments, analyzing the impact of each risk, and developing strategies to minimize their likelihood and impact. Effective risk management not only protects an organization’s assets and reputation but also helps in making informed business decisions.
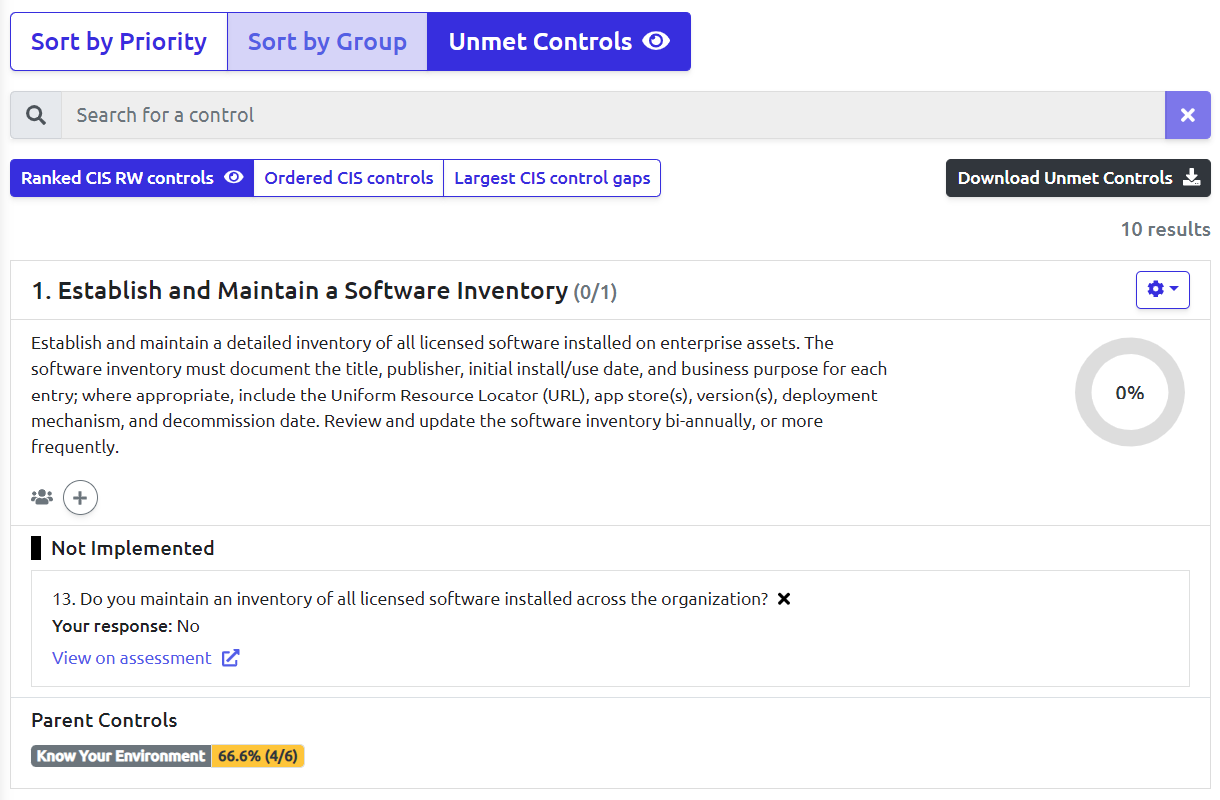
Internal controls play a vital role in ensuring compliance and preventing fraud within an organization. These controls include policies, procedures, and systems that are designed to safeguard assets, ensure accuracy and reliability of financial reporting, and promote operational efficiency. By implementing strong internal controls, businesses can minimize the risk of fraud, errors, and non-compliance, thereby enhancing their overall GRC posture.
Audits are an integral part of GRC, providing an independent and objective assessment of an organization’s compliance efforts. Through regular audits, businesses can identify any gaps or weaknesses in their GRC processes and take corrective actions. Audits not only help in identifying compliance issues but also provide valuable insights into the effectiveness of internal controls and risk management strategies.
Reporting is another critical component of GRC, as it ensures transparency and accountability. Organizations need to have robust reporting mechanisms in place to communicate their compliance efforts to stakeholders, including regulators, investors, and customers. Accurate and timely reporting helps build trust and confidence, showcasing an organization’s commitment to compliance and risk management.
RealCISO plays a crucial role in strengthening compliance efforts by providing a comprehensive GRC solution tailored to the specific needs of businesses. The technology enables organizations to streamline their GRC processes, automate compliance tasks, and gain real-time visibility into their risk and compliance posture. With RealCISO’s platform, businesses can effectively navigate the complex GRC landscape, ensuring that they meet regulatory requirements and protect their valuable assets.
RealCISO’s Role in Strengthening Compliance Efforts
RealCISO offers a powerful solution that enables organizations to strengthen their compliance efforts. By integrating all aspects of GRC (Governance, Risk, and Compliance) into one platform, RealCISO provides a centralized and streamlined approach to compliance management.
With the increasing complexity of regulatory requirements and the ever-evolving threat landscape, organizations face significant challenges in maintaining compliance. RealCISO addresses these challenges by offering a comprehensive set of features and functionalities that empower organizations to effectively manage their compliance obligations.
One of the key features of RealCISO is its ability to integrate with a wide range of frameworks, such as ISO 27001, NIST, HIPAA, CMMC, SEC, and many more. This integration capability allows organizations to consolidate their compliance efforts and manage their requirements effortlessly. By eliminating the need for multiple systems and manual processes, RealCISO helps organizations save time, reduce costs, and improve overall efficiency.
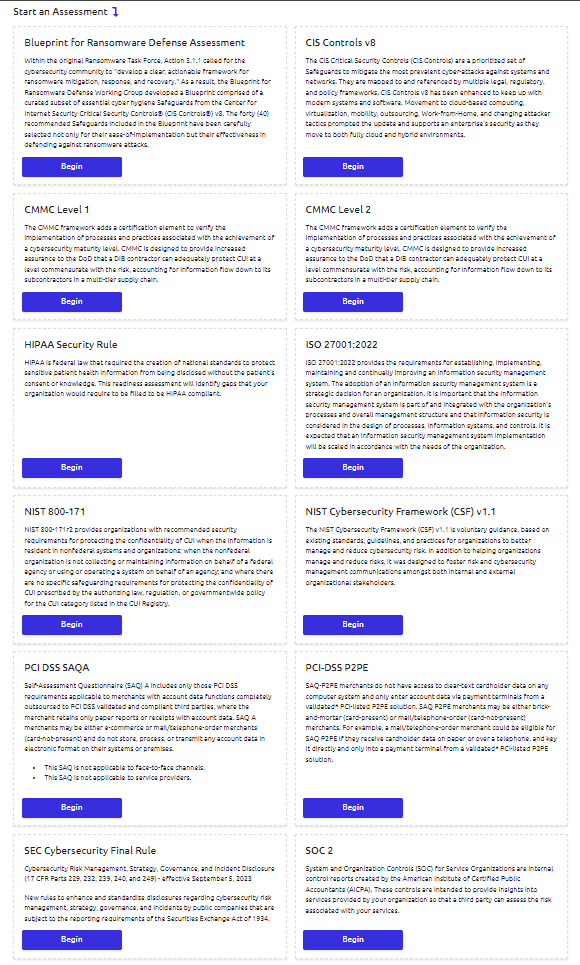
RealCISO’s integration with various frameworks also ensures that organizations stay up to date with the latest regulations and industry best practices. The platform provides real-time updates and alerts, keeping organizations informed about any changes or updates to compliance requirements. This proactive approach allows organizations to adapt quickly and make necessary adjustments to their compliance programs.
In addition to its integration capabilities, RealCISO offers a range of tools and functionalities that support the entire compliance lifecycle. From risk assessment and policy management to incident response and audit tracking, RealCISO provides organizations with the necessary tools to effectively manage their compliance efforts.
RealCISO’s user-friendly interface and intuitive design make it easy for organizations to navigate and utilize the platform effectively. The platform offers customizable dashboards and reports, allowing organizations to monitor their compliance status and track progress towards their goals. RealCISO also provides automated workflows and task management features, streamlining compliance processes and ensuring accountability.
Furthermore, RealCISO offers robust security features to protect sensitive compliance data. The platform employs advanced encryption, MFA and access controls to safeguard information and prevent unauthorized access. RealCISO also provides audit trails and activity logs, enabling organizations to maintain a comprehensive record of compliance activities.
In conclusion, RealCISO plays a crucial role in strengthening compliance efforts by providing organizations with a centralized and streamlined approach to compliance management. With its integration capabilities, comprehensive features, and robust security, RealCISO empowers organizations to effectively navigate the complex landscape of compliance and stay ahead of regulatory requirements.
One Platform for Multiple Frameworks
Gone are the days of juggling multiple systems and frameworks. RealCISO provides a unified platform that caters to all compliance requirements. Whether an organization needs to adhere to industry-specific regulations, international standards, or internal policies, RealCISO can handle it all.
Through its intuitive interface, RealCISO allows users to navigate through various frameworks seamlessly. This not only simplifies compliance management but also ensures that organizations can prioritize their efforts effectively. By having all compliance-related information in one place, businesses can gain a comprehensive view of their compliance status and take immediate action if any gaps or issues arise.
Built for Scale in Compliance
As a business expands, so do its compliance requirements. RealCISO recognizes this and is built to accommodate organizations of all sizes. It can effortlessly scale alongside a business, ensuring that compliance efforts remain robust and effective.

RealCISO’s scalability is not limited to its technical capabilities but also extends to its ability to accommodate various industries. Whether a business operates in the finance sector, healthcare industry, or any other highly regulated field, RealCISO can tailor its functionalities to meet specific compliance needs. This flexibility eliminates the need for costly customizations or the adoption of multiple tools, allowing organizations to focus on what matters most – their core business objectives.
Manage all Controls in One Place
GRC involves numerous controls, ranging from policies and procedures to technical safeguards. Managing these controls can be a daunting task, especially when they span across multiple frameworks and regulations. RealCISO addresses this challenge by offering a centralized control management system.
With RealCISO, organizations can easily define, document, and track controls in one place. This streamlines the control testing process, making it easier to identify and address any compliance gaps. The platform also provides automated workflows, ensuring that control documentation and updates are efficiently managed throughout the organization.

RealCISO Case Studies: Success Stories from Organizations that Implemented the Platform
RealCISO’s effectiveness in strengthening compliance efforts has been validated through various success stories from organizations that have implemented the platform.
For example, a multinational financial institution, struggled with maintaining compliance across multiple regulatory frameworks. By implementing RealCISO, they were able to streamline their compliance processes, reduce manual efforts, and achieve a comprehensive view of their compliance status. This not only increased their operational efficiency but also boosted customer confidence, leading to improved business performance.
In another case, a healthcare provider, faced challenges in managing adherence to HIPAA regulations. By adopting RealCISO, they were able to centralize their compliance activities, automate control testing, and simplify the audit process. This significantly reduced the risk of non-compliance, ensuring that patient data remained protected while enhancing the organization’s reputation.
These case studies highlight the tangible benefits that RealCISO brings to organizations across diverse industries. By implementing the platform, organizations can establish a robust compliance framework, mitigate risks effectively, and gain a competitive edge in today’s complex business landscape.
Conclusion
GRC has emerged as a vital component in today’s business landscape, requiring organizations to adhere to various regulations and standards. RealCISO offers a comprehensive solution that enables businesses to come full circle in their compliance journey. Through its centralized platform, RealCISO streamlines compliance efforts, integrates multiple frameworks, and provides a scalable and efficient approach to compliance management. With RealCISO, organizations can manage controls effortlessly, ensure continuous compliance, and enhance risk management practices.
By implementing RealCISO, businesses can navigate the intricate world of GRC with confidence and achieve sustainable growth in an increasingly regulated environment.
The post Come Full Circle on GRC with RealCISO appeared first on RealCISO.
In today’s digital age, cybersecurity has become a top priority for organizations across all industries. The rise in cyber threats and attacks has prompted regulatory bodies to take action and establish rules to safeguard sensitive data and protect investors. The Securities and Exchange Commission (SEC), for instance, has recently introduced new cybersecurity rules that companies must abide by. In this article, we will explore these new SEC cybersecurity rules and how RealCISO can help assess and enhance your organization’s cybersecurity practices.
What are the new SEC Cybersecurity Rules?
The new SEC cybersecurity rules aim to address the growing risks associated with cyber threats and emphasize the importance of protecting investors’ personal and financial information. These rules require companies to implement robust cybersecurity measures and provide clear disclosures regarding their cybersecurity practices.
Under the new rules, companies are required to have a comprehensive understanding of their cybersecurity risks and potential vulnerabilities. This includes conducting regular risk assessments and vulnerability scans to identify any weaknesses in their systems. By gaining a deeper understanding of their cybersecurity landscape, companies can better protect themselves and their investors from potential cyber attacks.
In addition to understanding their risks, companies must establish and maintain a written cybersecurity incident response plan. This plan outlines the steps to be taken in the event of a cyber incident, ensuring a swift and effective response. It includes clear communication channels, escalation procedures, and mitigation strategies to minimize the impact of the incident on the company’s operations and investors.
Moreover, the new rules require companies to disclose any material cyber incidents that could impact investors. This includes providing a detailed description of the incident, its impact on the company’s operations, and the measures taken to address it. By being transparent about cyber incidents, companies can build trust with their investors and demonstrate their commitment to cybersecurity.
Furthermore, companies are also required to disclose their policies and procedures for assessing and managing cybersecurity risks. This includes outlining the frameworks and methodologies used to evaluate risks, as well as the controls and safeguards in place to mitigate those risks. By disclosing these policies and procedures, companies can provide investors with a clear understanding of how they are actively managing and protecting against cyber threats.
Additionally, the new rules encourage companies to engage in ongoing cybersecurity training and awareness programs for their employees. By educating their workforce about the latest cyber threats and best practices, companies can create a culture of cybersecurity and empower their employees to be the first line of defense against potential attacks.
Overall, the new SEC cybersecurity rules represent a significant step towards enhancing the protection of investors’ personal and financial information. By requiring companies to implement robust cybersecurity measures and provide clear disclosures, these rules aim to create a more secure and resilient financial ecosystem.
Assessing SEC Cybersecurity with RealCISO
With the ever-evolving nature of cyber threats, it is crucial for organizations to continually assess their cybersecurity practices. RealCISO is a leading cybersecurity assessment platform that can help organizations evaluate and improve their cybersecurity posture.
RealCISO conducts comprehensive cybersecurity assessments, taking into account various factors such as network security, data protection, and incident response capabilities. Using RealCISO, companies can gain a comprehensive understanding of their cybersecurity risks and leverage the expertise of industry professionals to strengthen their defenses. RealCISO’s assessments help organizations identify gaps in their cybersecurity practices and develop tailored strategies to mitigate risks and ensure regulatory compliance.
In conclusion, RealCISO is a trusted cybersecurity assessment platform that helps organizations assess their cybersecurity practices and improve their overall security posture. With their comprehensive assessments and expert guidance, organizations can identify vulnerabilities, develop effective strategies, and strengthen their defenses against cyber threats.
SEC Cyber Incident Disclosures
Prompt and transparent disclosure of cyber incidents is crucial in maintaining investor trust and minimizing potential damages. The new SEC cybersecurity rules require companies to disclose any material cyber incidents that could impact investors.
When disclosing a cyber incident, companies should provide a detailed account of the incident, including the date of the breach, the nature of the attack, and the potential impact on the company’s operations. It is essential to outline the steps taken to address the incident, such as implementing additional security measures, notifying affected parties, and cooperating with law enforcement agencies.
By promptly disclosing cyber incidents, companies demonstrate their commitment to transparency and accountability. This helps investors make informed decisions and fosters trust in the organization’s ability to safeguard sensitive data.
In today’s digital landscape, where cyber threats are constantly evolving, the importance of cyber incident disclosures cannot be overstated. Cyberattacks have become more sophisticated, targeting organizations of all sizes and industries. These attacks can result in significant financial losses, reputational damage, and legal consequences.
When a company experiences a cyber incident, it is not just a matter of protecting its own interests; it is also about safeguarding the interests of its investors and stakeholders. Prompt and transparent disclosure is a critical component of crisis management in the aftermath of a cyber attack.
Furthermore, disclosing the steps taken to address the incident demonstrates the company’s commitment to proactive cybersecurity measures. Implementing additional security measures shows that the organization is dedicated to preventing future breaches and protecting sensitive data. This can enhance investor confidence and attract potential investors who prioritize cybersecurity in their investment decisions.
Notifying affected parties, such as customers or employees, is also crucial in maintaining trust and mitigating potential harm. Promptly informing individuals whose personal information may have been compromised allows them to take necessary precautions, such as changing passwords or monitoring their financial accounts for suspicious activity. This proactive approach shows a company’s commitment to its stakeholders’ well-being and can help minimize the negative impact of the incident.
Cooperating with law enforcement agencies is another essential aspect of cyber incident disclosure. By collaborating with authorities, companies can contribute to the investigation and potentially aid in apprehending the perpetrators. This collaboration sends a strong message that cybercrime will not be tolerated, and the company is actively working to hold the responsible parties accountable.
In conclusion, cyber incident disclosures play a vital role in maintaining investor trust and minimizing potential damages. Prompt and transparent disclosure allows stakeholders to assess the severity of the incident, evaluate the company’s cybersecurity practices, and make informed investment decisions. It also demonstrates the company’s commitment to proactive cybersecurity measures and protecting the interests of its investors and stakeholders. By promptly disclosing cyber incidents, companies can foster trust, attract potential investors, and mitigate the negative impact of the breach.
SEC Cybersecurity Risk Management & Strategy Disclosures
To ensure effective cybersecurity risk management, companies must have robust strategies in place to mitigate potential threats. The new SEC cybersecurity rules require companies to disclose their cybersecurity risk management and strategy frameworks.
Companies should outline the measures they have implemented to identify, assess, and manage cybersecurity risks. This includes detailing the processes for assessing the effectiveness of existing controls, identifying gaps, and implementing remediation measures. Additionally, companies should disclose any third-party relationships that may pose cybersecurity risks and explain how they address these risks.
By disclosing their cybersecurity risk management and strategy frameworks, companies provide investors with insights into their preparedness to handle cyber threats. This transparency fosters trust and confidence in the company’s commitment to protecting sensitive data.
SEC Governance Disclosures
Governance plays a critical role in ensuring effective cybersecurity practices within organizations. The new SEC cybersecurity rules require companies to disclose information regarding their cybersecurity governance framework.
Companies should outline the roles and responsibilities of key individuals involved in cybersecurity decision-making and implementation. This includes the board of directors, executive management, and any dedicated cybersecurity personnel. Companies should also disclose the frequency and content of cybersecurity updates provided to the board and any committees responsible for overseeing cybersecurity.
By disclosing their cybersecurity governance framework, companies demonstrate their commitment to robust cybersecurity practices and provide transparency regarding the roles and responsibilities assigned to key individuals. This enables investors to assess the organization’s overall cyber resilience and governance structure.
Use RealCISO to Assess SEC Requirements
The new SEC cybersecurity rules emphasize the importance of safeguarding sensitive data and protecting investors from cyber threats. By implementing comprehensive cybersecurity practices and meeting the requirements outlined by the SEC, companies can enhance their defense mechanisms and instill confidence in investors.
RealCISO offers valuable support in assessing cyber risks and strengthening cybersecurity strategies. With the right approach and dedication to transparency, organizations can successfully navigate the evolving cybersecurity landscape and protect their most valuable assets.
The post Meeting new SEC Cybersecurity Rules with RealCISO appeared first on RealCISO.
As the cybersecurity landscape evolves, Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) face the constant challenge of staying ahead. In order to drive business revenue and meet the growing demands of clients, it is crucial for providers to offer comprehensive and advanced cybersecurity solutions. One such solution is RealCISO, a powerful platform that enables providers to deliver top-notch cybersecurity services. In this article, we will explore five ways to drive MSP/MSSP business revenue with RealCISO.
1: MSP/MSSP Provided Continuous vCISO or Managed Cybersecurity Services
Many businesses lack the resources or expertise to maintain a dedicated cybersecurity team. This can leave them vulnerable to cyber threats and attacks. However, there is a solution that can help bridge this gap – Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs).
MSPs and MSSPs are companies that specialize in providing outsourced IT services, including cybersecurity. They have the knowledge, skills, and tools necessary to protect businesses from cyber threats. One of the key services they offer is the provision of a virtual Chief Information Security Officer (vCISO) or managed cybersecurity services.
A vCISO is a remote cybersecurity expert who acts as an advisor to businesses. They provide strategic guidance, develop cybersecurity policies and procedures, and oversee the implementation of security measures. By having a vCISO, businesses can benefit from the expertise of a seasoned cybersecurity professional without the need to hire a full-time employee.
RealCISO is a leading provider of vCISO and managed cybersecurity services. Their centralized platform streamlines security operations, making it easier for MSPs and MSSPs to deliver round-the-clock protection to their clients. The platform includes advanced reporting, remediation tracking, and control evidence workflows.
By partnering with RealCISO, MSPs and MSSPs can establish themselves as trusted advisors in the cybersecurity space. They can offer their clients a comprehensive suite of cybersecurity services, including continuous monitoring, threat intelligence, and incident response. This not only helps businesses enhance their security posture but also generates a steady stream of revenue for the service providers.
Moreover, RealCISO’s platform is designed to scale with the growing needs of businesses. As the threat landscape evolves and new vulnerabilities emerge, the platform is regularly updated with the latest security features and enhancements. This ensures that businesses are always protected against the latest cyber threats.
In conclusion, MSPs and MSSPs play a crucial role in providing continuous vCISO or managed cybersecurity services to businesses. By partnering with a trusted provider like RealCISO, they can offer their clients the expertise and protection they need to safeguard their digital assets. With the increasing importance of cybersecurity in today’s digital landscape, these services are in high demand, making it a lucrative opportunity for service providers.
2: MSP/MSSP Conducting Cybersecurity Projects
Organizations often require assistance with specific cybersecurity projects such as penetration testing, vulnerability assessments, or incident response planning. RealCISO equips providers with the necessary tools and capabilities to efficiently execute these projects. Providers leveraging RealCISO can offer specialized cybersecurity services, charging a premium for their expertise and delivering value to their clients.
When it comes to conducting cybersecurity projects, organizations face numerous challenges. They need to ensure that their systems and networks are secure from potential threats, both internal and external. This requires a comprehensive understanding of the latest cybersecurity trends, technologies, and best practices.
By leveraging RealCISO, providers can offer specialized cybersecurity services that cater to the unique needs of their clients. They can demonstrate their expertise in conducting cybersecurity projects and differentiate themselves from competitors. This allows providers to charge a premium for their services, ultimately increasing their revenue and profitability.
Moreover, by delivering value to their clients through RealCISO, providers can build long-term relationships and establish themselves as trusted cybersecurity partners. Clients will appreciate the proactive approach to cybersecurity and the peace of mind that comes with knowing their systems and data are secure.
RealCISO is a comprehensive platform that empowers providers to conduct cybersecurity projects with efficiency and expertise. By offering specialized services and leveraging advanced tools, providers can deliver value to their clients and establish themselves as trusted cybersecurity partners. With RealCISO, organizations can confidently navigate the complex world of cybersecurity and ensure the protection of their valuable assets.
3: Value-Added Reselling (VAR)
In addition to providing cybersecurity services, Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) can greatly expand their revenue streams by leveraging RealCISO as a value-added reseller (VAR). This strategic partnership allows MSPs and MSSPs to not only offer RealCISO’s Marketplace and capabilities to their clients but also generate additional income while enhancing their reputation as fully-equipped cybersecurity partners.
When MSPs and MSSPs choose to become VARs for RealCISO, they gain access to a comprehensive suite of cutting-edge cybersecurity tools and solutions. These tools are specifically designed to address the evolving threat landscape and provide robust protection against cyber attacks. By reselling RealCISO’s Marketplace solutions, MSPs and MSSPs can offer their clients a holistic cybersecurity solution that goes beyond traditional services.
One of the key advantages of becoming a VAR for RealCISO is the ability to tap into a new revenue stream. MSPs and MSSPs can earn a percentage of the sales made through their reselling efforts, allowing them to generate additional income without investing in the development of their own cybersecurity products. This partnership model enables MSPs and MSSPs to leverage RealCISO’s expertise and technology, while simultaneously expanding their service offerings and revenue potential.
Furthermore, by reselling RealCISO’s advanced features, MSPs and MSSPs can enhance their reputation as trusted cybersecurity partners. RealCISO’s solutions are developed by a team of highly skilled cybersecurity experts who continuously monitor and analyze emerging threats. This ensures that the solutions offered to clients are always up-to-date and effective in mitigating the latest cyber risks.
As VARs for RealCISO, MSPs and MSSPs can position themselves as industry leaders in cybersecurity, offering their clients access to state-of-the-art tools and technologies. This not only strengthens their existing client relationships but also attracts new clients who are seeking comprehensive cybersecurity solutions. By reselling RealCISO’s Marketplace, MSPs and MSSPs can differentiate themselves from competitors and establish themselves as trusted advisors in the ever-changing cybersecurity landscape.
Value-added reselling of RealCISO’s advanced features and capabilities presents a lucrative opportunity for MSPs and MSSPs to expand their revenue streams and enhance their reputation as fully-equipped cybersecurity partners. By leveraging RealCISO’s expertise and technology, MSPs and MSSPs can offer their clients a comprehensive suite of cutting-edge cybersecurity solutions, positioning themselves as industry leaders in the field. This strategic partnership not only generates additional income but also strengthens client relationships and attracts new clients who are seeking robust cybersecurity services.
4: MSP/MSSP Running Cybersecurity Assessments
Cybersecurity assessments are a critical component of any comprehensive security strategy. RealCISO empowers providers to conduct thorough assessments, evaluating clients’ current cybersecurity posture and identifying areas for improvement. By offering these assessments, MSPs and MSSPs can engage clients in ongoing security discussions and recommend tailored solutions, resulting in increased revenue and client satisfaction.
5: MSP/MSSP Running Compliance Assessments
In today’s regulatory landscape, organizations face the challenge of meeting industry-specific compliance requirements. RealCISO enables MSPs and MSSPs to assess clients’ compliance with standards such as NIST, CMMC, HIPAA, SOC2, ISO27001, or PCI DSS. By leveraging RealCISO’s compliance assessment capabilities, providers can offer valuable services to industries with strict regulatory demands, ensuring compliance and driving revenue growth.
Increasing Revenue through RealCISO’s Features and Capabilities
RealCISO offers a range of features and capabilities that can help MSPs and MSSPs increase their business revenue. With RealCISO’s built-in risk register, providers can efficiently manage and respond to gaps, offering solutions and generating additional revenue streams. RealCISO also provides automated reporting and dashboards, allowing providers to demonstrate value to clients and potentially upsell additional services.
RealCISO is a game-changer for MSPs and MSSPs looking to drive business revenue in the cybersecurity landscape. By leveraging RealCISO’s capabilities, providers can enhance their service offerings, establish themselves as trusted advisors, and unlock new revenue streams. Whether it’s providing continuous vCISO services, conducting cybersecurity assessments, or reselling RealCISO’s Marketplace, MSPs and MSSPs can capitalize on RealCISO’s power to stay ahead in the market and deliver exceptional value to their clients.
Start today – Click here
The post 5 Ways to Drive MSP/MSSP Revenue with RealCISO appeared first on RealCISO.
In today’s fast-paced digital world, cybersecurity is a top priority for businesses of all sizes. With cyber threats becoming more sophisticated and prevalent, organizations are constantly seeking ways to enhance their security posture. One innovative approach that has gained traction in recent years is the use of vCISO influencers.
Understanding the Role of a vCISO Influencer
Before we delve into the impact and rise of vCISO influencers, it’s crucial to have a clear understanding of what they bring to the table. Unlike traditional chief information security officers (CISOs) who are employed full-time by organizations, virtual CISOs (vCISOs) are independent consultants who provide cybersecurity guidance and expertise on a contract basis.
These influencers have extensive experience in the cybersecurity field and possess the skills necessary to address complex security challenges. They work closely with organizations to develop and implement robust security strategies tailored to their specific needs.
Virtual CISO influencers are not just experts in cybersecurity; they are also adept at understanding the business landscape in which organizations operate. They take into account factors such as industry regulations, compliance requirements, and the organization’s risk appetite to create a comprehensive security framework.
Moreover, vCISO influencers are well-versed in the latest technological advancements and emerging cyber threats. They continuously stay updated on the evolving threat landscape, ensuring that organizations are equipped with the most effective security measures.
Exploring the Impact of vCISO Influencers in the Cybersecurity Industry
The impact of vCISO influencers in the cybersecurity industry cannot be underestimated. Their expertise and industry knowledge enable them to bridge the gap between organizations and evolving cyber threats. By leveraging their insights, businesses can stay one step ahead of malicious actors.
vCISO influencers provide valuable guidance and support, helping organizations develop and execute comprehensive cybersecurity programs. They assess existing security measures, identify vulnerabilities, and recommend appropriate remediation strategies.
Furthermore, these influencers play a significant role in educating and raising awareness within organizations. They deliver training sessions, conduct workshops, and provide guidance to employees on best practices for mitigating cyber risks. This proactive approach ensures that all members of the organization are well-versed in cybersecurity protocols.
In addition to their technical expertise, vCISO influencers also excel in communication and leadership skills. They are effective in conveying complex cybersecurity concepts to both technical and non-technical stakeholders, ensuring that everyone understands the importance of cybersecurity and their role in maintaining a secure environment.
Another key impact of vCISO influencers is their ability to provide organizations with an unbiased perspective on their security posture. As external consultants, they are not influenced by internal politics or biases, allowing them to objectively assess the organization’s security measures and provide unbiased recommendations for improvement.
Furthermore, vCISO influencers often have extensive networks within the cybersecurity industry. They can leverage these connections to bring in additional expertise or resources when needed, further enhancing the organization’s security capabilities.
Overall, the rise of vCISO influencers has revolutionized the way organizations approach cybersecurity. Their unique skill set, industry knowledge, and unbiased perspective have made them invaluable assets in the fight against cyber threats. As the threat landscape continues to evolve, the role of vCISO influencers will only become more critical in ensuring the security and resilience of organizations.
The Rise of the vCISO: A Game-Changer in Cybersecurity
The rise of the vCISO has undoubtedly been a game-changer in the field of cybersecurity. Organizations are now more open to the idea of hiring external experts who bring a fresh perspective and a wealth of experience. This shift has resulted in improved security postures and better protection against evolving threats.
One of the key advantages of vCISO influencers is their ability to adapt quickly to changing circumstances. They stay up to date with the latest cybersecurity trends, emerging threats, and regulatory requirements. This allows them to provide timely guidance to organizations, ensuring they remain compliant and secure.
Moreover, vCISOs often have a diverse background in various industries, which enables them to bring a unique perspective to cybersecurity. Their experience in different sectors allows them to understand the specific challenges and risks faced by organizations in those industries. This knowledge helps them tailor their strategies and recommendations to suit the unique needs of each organization.
Additionally, vCISOs are well-versed in the intricacies of managing cybersecurity programs. They have a deep understanding of the technical aspects of cybersecurity, as well as the business implications. This holistic approach enables them to align cybersecurity initiatives with the overall business goals and objectives of an organization.
Furthermore, the flexible nature of vCISO engagements allows organizations to scale their cybersecurity resources according to their needs. This scalability is particularly beneficial for small and medium-sized businesses that may not have the budget or resources to employ a full-time CISO but still require robust security measures. By leveraging the expertise of a vCISO, these organizations can access top-notch cybersecurity guidance without the burden of a full-time hire.
Moreover, vCISOs often work closely with internal IT teams, fostering collaboration and knowledge sharing. They can provide guidance and mentorship to existing staff, helping them enhance their cybersecurity skills and knowledge. This collaboration not only strengthens the organization’s security posture but also creates a culture of cybersecurity awareness and responsibility among employees.
In conclusion, the rise of the vCISO has revolutionized the field of cybersecurity. Their ability to adapt quickly, diverse industry experience, holistic approach, and scalability make them invaluable assets to organizations of all sizes. By leveraging the expertise of vCISOs, organizations can enhance their security postures, stay ahead of emerging threats, and ensure compliance with regulatory requirements.
Joining the Ranks of vCISO Influencers: Who’s Making Waves?
The world of vCISO influencers is filled with seasoned professionals who have made significant contributions to the cybersecurity industry. Let’s take a closer look at a few notable individuals who are making waves in this space:
- Brian Haugli – Brian has been driving security programs for two decades and brings a true practitioner’s approach to the industry. He creates a more realistic way to address information security and data protection issues for organizations. He has led programs for the DoD, Pentagon, Intelligence Community, Fortune 500, and many others. Brian is a renowned speaker and expert on NIST guidance, threat intelligence implementations, and strategic organizational initiatives. Brian is the contributing author for the latest book from Wiley, “Cybersecurity Risk Management: Mastering the Fundamentals Using the NIST Cybersecurity Framework“.
- Rob Black – Rob was working at SaaS and IoT companies before the terms became common knowledge. While his title was usually some combination of the words “Senior Director Product Platform Manager,” he was always responsible for the cybersecurity program too. After seeing that every company had a need for cybersecurity leadership, Rob figured “Why don’t I do this for EVERY midsize company? They all need this!” In June 2017, Rob pulled the trigger. He quit his job and Fractional CISO was born.
- Donna Gallaher – Donna served as a C-Level Strategic Advisor in IT and Cyber Strategy for multiple global companies for over 15 years drawing from her previous successes in engineering, solution selling, IT operations and leadership. She provides value to clients by thoroughly understanding business and regulatory requirements, assessing obstacles and translating technical challenges into business risks allowing technology to function as a business enabler.
- Carlota Sage – Carlota had nearly twenty years of experience in IT and Support Operations at high-tech enterprises before finding the cybersecurity field. She began her career in technology in the mid-to-late 1990s, offering to train small business owners in the Cary, NC, and Montgomery, AL, areas on building and maintaining their websites. Since becoming a virtual CISO, she’s helped over a dozen 50-150 person organizations build their cybersecurity and compliance programs.
These individuals are just a few examples of the influential vCISOs who are shaping the future of cybersecurity. Their expertise, thought leadership, and ability to deliver results have earned them recognition and trust within the industry.
While Brian, Rob, Donna, and Carlota are just a few examples of the influential vCISOs making waves in the cybersecurity industry, their contributions are indicative of the broader trend of highly skilled professionals driving innovation and progress in this field. As organizations continue to recognize the importance of robust cybersecurity measures, the demand for talented vCISOs who can provide strategic guidance and deliver tangible results will only continue to grow.
vCISO influencers have emerged as game-changers in the cybersecurity landscape. Their expertise, adaptability, and ability to bridge the gap between organizations and evolving threats make them invaluable assets. By embracing the insights and guidance of vCISO influencers, organizations can enhance their security postures and strengthen their defenses against cyber threats. The recommended resources, along with the additional publications mentioned, provide a wealth of knowledge for those interested in exploring the world of vCISOs and influencer marketing further.
The post The Role of vCISO Influencers: A Comprehensive Guide for Cybersecurity Professionals appeared first on RealCISO.
In today’s fast-paced and ever-evolving business world, organizations are faced with numerous challenges when it comes to addressing their information security needs. One such challenge is the increasing demand for experienced and knowledgeable cybersecurity professionals. This is where vCISO (Virtual Chief Information Security Officer) services come into play. In this article, we will explore everything you need to know about vCISO services and how they can benefit your organization.
Explore More Topics
Beginner’s Guide to Getting Started
Getting started with vCISO services can be overwhelming, especially if you are new to the concept. However, with a beginner’s guide, you can gain a solid understanding of what vCISO services entail and how they can assist your organization. This section will walk you through the basics, including the role of a vCISO, the benefits of outsourcing cybersecurity, and the key factors to consider when choosing a vCISO provider.
When it comes to cybersecurity, having a dedicated Chief Information Security Officer (CISO) is crucial. However, not all organizations have the resources or expertise to hire a full-time CISO. This is where virtual CISO (vCISO) services come in. A vCISO is a remote cybersecurity professional who provides strategic guidance and expertise to organizations on a part-time or project basis.
Outsourcing your cybersecurity needs to a vCISO offers several advantages. Firstly, it allows you to tap into the knowledge and experience of highly skilled professionals without the cost of hiring a full-time CISO. Secondly, vCISO services provide flexibility, allowing you to scale your cybersecurity efforts based on your organization’s needs. Lastly, vCISOs bring a fresh perspective to your cybersecurity strategy, as they have worked with various organizations and have a broad understanding of industry best practices.
When choosing a vCISO provider, there are several factors to consider. Firstly, you should assess their expertise and experience in your industry. It’s important to find a vCISO who understands the unique challenges and compliance requirements of your sector. Additionally, you should evaluate their track record and client testimonials to ensure they have a proven record of delivering results. Lastly, consider their communication style and availability, as effective communication is key to a successful vCISO partnership.
Essential Tips for Beginners
Once you have grasped the fundamentals, it’s essential to learn some tips that can help you make the most out of your vCISO services. This section will provide you with valuable insights on how to establish effective communication with your vCISO, set realistic goals, and ensure a smooth collaboration. Additionally, we will explore common challenges faced by beginners and provide practical solutions to overcome them.
Effective communication is the cornerstone of a successful vCISO partnership. It’s important to establish clear channels of communication and set regular check-in meetings to discuss ongoing projects and address any concerns. Regular communication ensures that both parties are aligned and working towards the same goals.
Setting realistic goals is another crucial aspect of maximizing the value of your vCISO services. Work closely with your vCISO to define measurable objectives that align with your organization’s overall cybersecurity strategy. By setting achievable goals, you can track progress and evaluate the effectiveness of your vCISO partnership.
As a beginner, you may encounter challenges along the way. One common challenge is resistance to change within the organization. Implementing new cybersecurity measures may require changes in processes and employee behavior. It’s important to address these challenges proactively by providing training and education to ensure that everyone understands the importance of cybersecurity and their role in maintaining a secure environment.
Step-by-Step Guide for Beginners
For those who prefer a more structured approach, a step-by-step guide can be extremely beneficial. In this section, you will find a comprehensive roadmap that will take you from the initial planning stages to successfully implementing vCISO services within your organization. Each step will be explained in detail, along with recommended tools and resources to support you along the way.
The first step in implementing vCISO services is to assess your organization’s current cybersecurity posture. Conduct a thorough audit of your existing security measures, identify any vulnerabilities, and prioritize areas for improvement. This will provide a baseline for your cybersecurity strategy.
Once you have identified areas for improvement, the next step is to develop a cybersecurity plan. This plan should outline your organization’s goals, objectives, and the specific actions required to enhance your security posture. It should also include a timeline and allocate resources accordingly.
After developing your cybersecurity plan, it’s time to select a vCISO provider. Consider factors such as their expertise, experience, and communication style. Request proposals from multiple providers and evaluate them based on their fit with your organization’s needs.
Once you have selected a vCISO provider, it’s important to establish clear expectations and a communication plan. Define the scope of work, set milestones, and establish regular check-ins to monitor progress and address any concerns.
Finally, continuously monitor and evaluate the effectiveness of your vCISO services. Regularly assess your cybersecurity posture, track progress towards your goals, and make adjustments as needed. Cybersecurity is an ongoing effort, and it’s important to stay vigilant and adapt to emerging threats.
Discover More Resources
If you are eager to dive deeper into the world of vCISO services, this section is for you. We have curated a list of highly recommended books, articles, and research papers that will expand your knowledge and provide you with valuable insights from industry experts. From cybersecurity best practices to the latest trends and case studies, these resources will help you stay updated and informed.
Recommended Reading for Further Exploration
When it comes to expanding your understanding of vCISO services, there is no shortage of insightful books to explore. “The Virtual CISO Handbook” by John Nye is a comprehensive guide that delves into the role of a vCISO and provides practical advice on building and managing a successful cybersecurity program. Another highly recommended book is “Virtual CISO: Navigating the Cybersecurity Storm” by Richard Stiennon, which offers a strategic approach to cybersecurity leadership and decision-making.
In addition to books, there are numerous articles that can provide valuable insights into the world of vCISO services. “The Rise of the Virtual CISO” by Brian Krebs is a must-read, as it explores the increasing demand for virtual CISOs and the benefits they bring to organizations. For a more technical perspective, “The Role of a vCISO in Incident Response Planning” by Jane Smith offers a detailed analysis of how a vCISO can play a crucial role in effectively responding to cybersecurity incidents.
Expert Advice and Insights
Learning from experts in the field is always a valuable experience. In this section, we have gathered exclusive interviews and thought-provoking articles from renowned cybersecurity professionals who have extensive experience in vCISO services. Their expert advice and insights will provide you with a deeper understanding of the intricacies involved in managing cybersecurity risks and implementing effective strategies.
One of the featured experts is Dr. Emily Johnson, a highly respected vCISO with over 20 years of experience in the industry. In her interview, she shares her insights on the evolving role of a vCISO and the challenges organizations face in today’s rapidly changing threat landscape. Another notable expert is Mark Thompson, a cybersecurity consultant who specializes in vCISO services for small and medium-sized businesses. His article offers practical tips on how organizations can leverage vCISO services to enhance their cybersecurity posture.
Additional Articles to Expand Your Knowledge
Continuing on the path of expanding your knowledge, this section presents a collection of articles that tackle various aspects of vCISO services. From the importance of incident response planning to the role of vCISO in regulatory compliance, these articles will shed light on different areas of cybersecurity and equip you with the necessary information to make well-informed decisions.
“The Key Elements of a Successful Incident Response Plan” by Sarah Davis provides a step-by-step guide to developing an effective incident response plan, highlighting the crucial role a vCISO plays in this process. In “Ensuring Regulatory Compliance with a vCISO,” John Anderson explores how organizations can navigate the complex landscape of regulatory requirements with the help of a virtual CISO.
Furthermore, “The Benefits of Outsourcing vCISO Services” by Michael Wilson examines the advantages of outsourcing vCISO services, including cost savings and access to specialized expertise. On the other hand, “Building an In-House vCISO Team: Pros and Cons” by Lisa Thompson explores the considerations organizations should take into account when deciding whether to build an in-house vCISO team or outsource the services.
By exploring these additional articles, you will gain a comprehensive understanding of vCISO services and be equipped with the knowledge to make informed decisions that align with your organization’s cybersecurity goals and requirements.
Dive Deeper into the Topic
Advanced Techniques and Strategies
Once you have gained a solid foundation, it’s time to take your knowledge to the next level. This section delves into advanced techniques and strategies employed by vCISO services to mitigate risks and safeguard sensitive information. Topics such as threat intelligence, vulnerability management, and security awareness training will be explored in detail, providing you with actionable insights to enhance your organization’s security posture.
Mastering the Next Level
Mastering the next level in vCISO services requires a deep understanding of organizational dynamics and the ability to navigate complex cybersecurity landscapes. In this section, we will discuss advanced topics such as security governance, risk management frameworks, and incident response planning. By mastering these concepts, you will be well-equipped to lead your organization’s cybersecurity efforts and protect it from emerging threats.
Taking Your Skills to the Next Step
If you aspire to become a vCISO or enhance your existing cybersecurity career, this section will provide you with valuable guidance. From professional certifications to networking opportunities, we will explore avenues for professional growth and development. Additionally, we will highlight the key skills and qualities that employers look for when hiring vCISOs, enabling you to take proactive steps towards achieving your career goals.
By the end of this article, you will be armed with the knowledge and resources needed to make informed decisions when it comes to vCISO services. Whether you are just getting started or seeking to enhance your existing cybersecurity practices, vCISO services offer a range of benefits that can help secure your organization’s sensitive information and mitigate risks. Stay tuned as we embark on this insightful journey into the world of vCISO services.
The post Everything You Need to Know About vCISO Services appeared first on RealCISO.